Tired of cybersecurity predictions that read like science fiction? You're not alone. In a whirlwind of AI hype and zero-day scares, it's easy to lose sight of the bedrock principles that truly safeguard our digital world. This isn't about predicting the future; it’s about understanding the present. Join us as we unpack the wisdom of Merritt Baer, former Deputy CISO at AWS and current CISO at Reco.AI, in a discussion that cuts through the noise to focus on what's actually going to make a difference in 2025 and beyond.
The Unchanging Truths: Why the Basics Still Matter
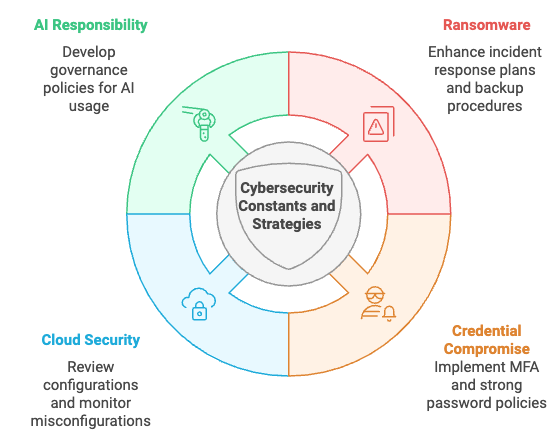
Forget the flashy new tools for a minute. What if we focused on the evergreen challenges that are constantly testing our defenses? As Jeff Bezos wisely asked, “What’s going to stay the same?” In cybersecurity, this means recognizing that some battles are fought on familiar ground. Merritt highlights these constants:
Ransomware isn't going anywhere. It's not just a nuisance; it’s a sophisticated operation involving both criminal gangs and nation-states using it as a revenue stream.
Tactical Recommendation: Enhance incident response plans to include specific ransomware scenarios. Implement robust backup and recovery procedures, and ensure they're regularly tested.
Credential compromise is still the front door. Forget the complex hacks; most attackers are simply walking in with stolen or misused credentials.
Tactical Recommendation: Implement multi-factor authentication (MFA) across all systems and applications. Enforce strong password policies and implement regular password resets. Consider behavioral analytics to detect unusual login patterns.
The cloud shared responsibility model is here to stay. You are responsible for security in the cloud. This isn't just about AWS; it applies to all cloud providers.
Tactical Recommendation: Conduct regular reviews of cloud configurations and permissions. Ensure your team is well-versed in the shared responsibility model and its nuances. Use tools to monitor and alert on misconfigurations.
The shared responsibility model extends to AI. As we bring AI into our environments, we must address that there is a shared responsibility with the AI, the hosting company and the end user.
Tactical Recommendation: Develop a clear framework for AI usage. Define who is responsible for the security of the data being fed into and generated by AI models. Implement governance policies for the usage of AI tools and services.
The Shifting Sands: Navigating AI, Regulations, and Supply Chains
While some things remain constant, the cybersecurity landscape is perpetually evolving. Here are the key areas where we need to be adaptable:
The AI Revolution (and its challenges): AI is transforming both security and threat landscapes. While AI offers incredible potential for automation, it also introduces shadow AI risks.
Tactical Recommendation: Implement a formal program to identify and manage shadow AI risks. This includes discovering which AI tools and services employees are using. Create policies for responsible AI usage. Consider AI security tools such as Encrypt AI, which can be used to create guardrails for the usage of AI by employees.
Regulatory Pressures are Increasing: The SEC and DOJ are increasing their focus on CISO responsibilities. CISOs must adopt a reasonable, attestable, and defensible approach. This includes transparency with regulators, as misrepresenting the maturity of security programs can lead to significant issues.
Tactical Recommendation: Develop a clear, concise, and well-documented security program. Ensure that all security controls are properly implemented and regularly tested. Maintain accurate records of security incidents and breaches. When in doubt, file.
Supply Chain Vulnerabilities Persist: The Software Bill of Materials (SBOM) is a step in the right direction but is not a panacea. Understanding your vendors is important. The reality is that your biggest vulnerability is not in the software but it is likely with the people.
Tactical Recommendation: Develop a robust vendor risk management program. Conduct regular security assessments of all third-party vendors. Use SBOMs to track the components of your software, and ensure a process to patch identified vulnerabilities.
Security and Sustainability Intersect: Environmental concerns are increasingly linked to security.
Tactical Recommendation: Adopt sustainable security practices. Optimize data retention policies to reduce storage costs and environmental impact. Utilize spot instances or caching things at the edge.
CISOs: Charting the Course for 2025 and Beyond
As CISOs, we need to cut through the noise and focus on what truly matters. Here are actionable strategies for navigating the next year:
Embrace Contextualization: Focus on the context of your organization rather than generic solutions. Understand your specific industry, assets, and risk appetite. Focus on understanding patterns of behavior and access.
Tactical Recommendation: Develop a customized risk assessment framework for your specific organization. Identify the critical assets and the potential threats that are most relevant to your business.
AI: Don’t Fear it, Control It: AI is a powerful tool, but it is not infallible. Focus on a repeatable, attestable, and defensible approach. AI should be used to augment and empower human decision-making, not replace it entirely.
Tactical Recommendation: Implement a robust AI governance framework. Ensure that all AI systems are properly tested and validated. Create clear policies for the responsible use of AI.
Shared Responsibility is Key: Understand and embrace your responsibilities in the cloud, and when working with AI tools. Recognize that the shared responsibility model is also true for all apps in your environment.
Tactical Recommendation: Conduct regular training for all employees about their responsibilities in the shared responsibility model. This includes the cloud and AI tools. Use tools to track where your data resides.
Guardrail AI Use: Implement controls, policies, and processes to effectively manage the use of AI. This includes both technical and policy-based controls. AI tools need to be managed both at the enterprise level and at the personal level.
Tactical Recommendation: Implement policies that guide the appropriate use of AI tools and services. Ensure that all AI-generated content is reviewed and validated by a human. Consider the use of tools like Encrypt AI that allows you to set parameters for how your employees are using AI.
The Human Element: The Heart of Cybersecurity
In the end, cybersecurity is about humans. As Merritt reminds us, “We’re still building tech by humans for humans.” Technology, including AI, should serve humanity, and it's our job to ensure that it does. We must remain vigilant against threats, while also embracing the potential of these technologies. The key to navigating the complex cybersecurity landscape is to stay focused on what truly matters: effective risk management and a culture of security.
What's your take? What strategies are you focusing on in the year ahead? Share your insights in the comments below!
Thanks to our Sponsors this week
1) ThreatLocker - Do zero-day exploits and supply chain attacks keep you up at night? Worry nomore, harden your security with ThreatLocker. Worldwide, companies trust ThreatLocker to secure their data and keep their business operations moving.
ThreatLocker takes a deny-by-default approach to cybersecurity and provides a full audit of every action, allowed or blocked, for risk management and compliance. Onboarding and operation is fully supported by their US-based Cyber Hero support team.
2) CruiseCon - Ready to connect with top cybersecurity leaders? Set sail with CISO Tradecraft at CruiseCon, February 8-13, 2025! CruiseCon offers a unique blend of professional development and networking, it also provides valuable insights into navigating the ever-changing cybersecurity landscape.👇Use code CISOTRADECRAFT10 at CruiseCon.com for 10% off registration!