Are you ready to secure the AI frontier? The winds of change have swept through U.S. AI policy, and now, cybersecurity executives are the vanguards of AI safety. It's time to ditch the passenger seat and grab the steering wheel! Recent Executive Orders (EOs) have ushered in an era of deregulation, placing the onus of AI security squarely on your shoulders.
Decoding the Executive Orders on AI
Let's dissect the pivotal EOs that shape your new reality:
EO 13859 (2019): This order kickstarted the American AI Initiative, prioritizing AI research and development. Federal agencies were encouraged to pump investments into AI, but security mandates were noticeably absent. The result? Accelerated AI adoption and an expanded attack surface.
EO 13960 (2020): The focus shifted to trustworthy AI in federal agencies, emphasizing accountability and risk management. Early risk management expectations for AI systems emerged, along with a push for explainability and governance. CISOs were now expected to ensure that AI applications aligned with ethical standards and didn't compromise security.
EO 14028 (2021): A cybersecurity powerhouse, this EO fortified U.S. cybersecurity defenses. Zero trust security, software supply chain security, and multi-factor authentication (MFA) became mandatory. Supply chain vigilance, incident response planning, and cloud security took center stage.
EO 14110 (2023): A national framework for AI security, ethics, and privacy was established, mandating AI safety testing and audits for high-risk applications.
EO 14148 (2025): The rug was pulled out from under EO 14110, signaling a halt to government-mandated AI safety regulations.
EO 14179 (2025): Policies perceived as barriers to AI innovation were dismantled, shifting the focus from secure AI to unleashing innovation.
EO 14144 (2025): Innovation in the nation's cybersecurity was strengthened and promoted, remaining unaffected by the change in administration.
The CISO's Call to Action: A New Era of Leadership
With EO 14110 rescinded, government-led AI safety regulations are on ice. This deregulation thrusts CISOs into the driver's seat, tasking them with defining their organization's AI security standards. Ethical AI and cybersecurity morph into corporate responsibilities, demanding that CISOs guide their executive teams in addressing these critical concerns.
Your Prescriptive Battle Plan: Securing the AI Realm
Here's your actionable guide to navigating this uncharted territory:
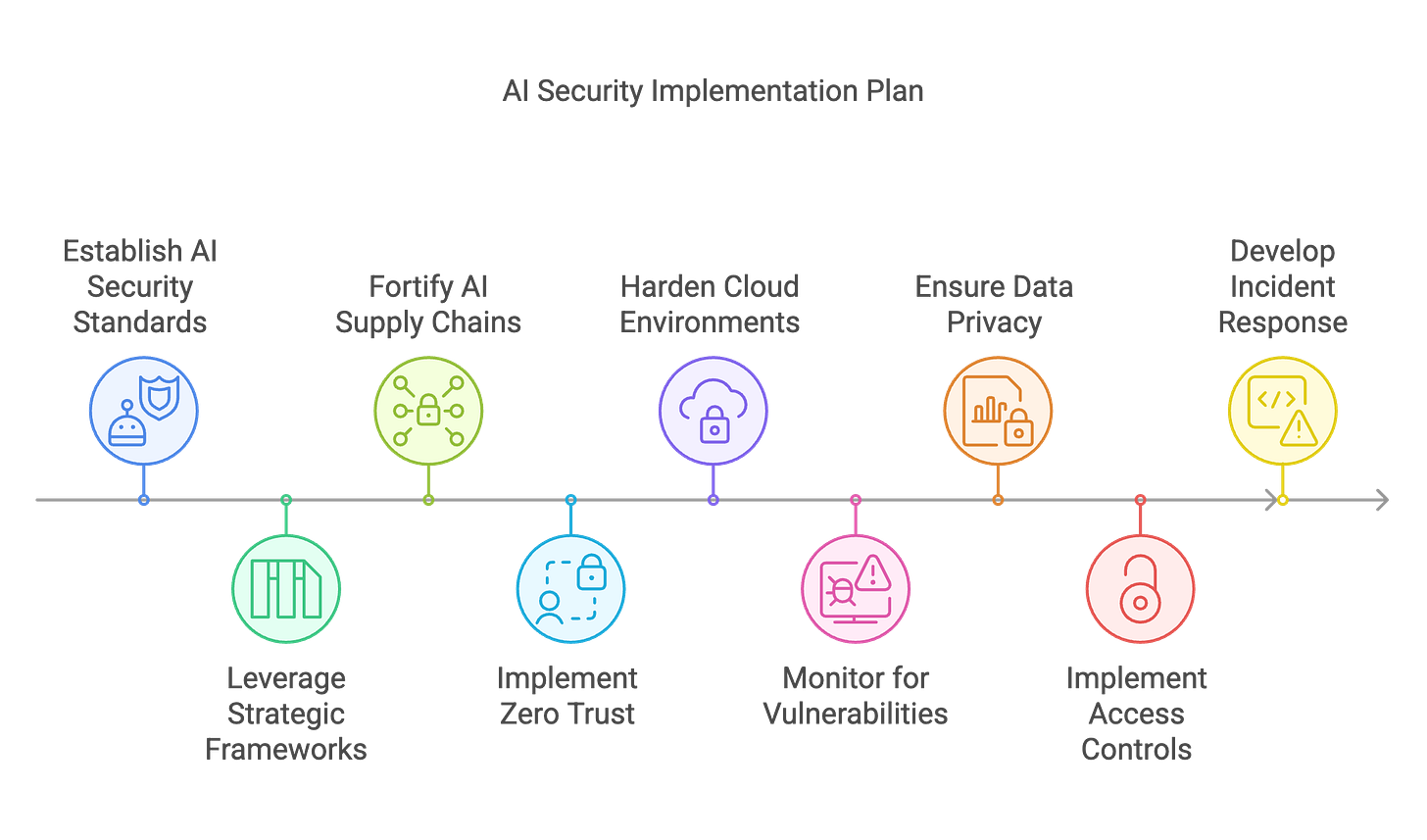
Establish Unshakeable Internal AI Security Standards: Don't await government mandates; forge your own path. Start by defining a comprehensive AI security policy that aligns with your organization's risk appetite and business objectives.
Strategic Framework Leveraging: Utilize established government risk frameworks like NIST, CIS Controls, and FedRAMP as building blocks for your standards.
Fortify AI Supply Chains and Software Development: Implement stringent security assessments, demanding security attestations from vendors. Align AI development with the NIST Secure Software Development Framework (SSDF).
Demand Software Bills of Materials (SBOMs) from your software providers.
Participate in the CISA Repository for Software Attestation and Artifacts (RSAA) to ensure your software providers adhere to secure development practices.
Zero Trust Implementation: Enforce zero trust identity frameworks and phishing-resistant MFA for all AI-related systems.
Adopt innovative identity technologies like phishing-resistant authentication.
Pilot deployment of WebAuthn or hardware tokens like YubiKeys to reduce phishing risks.
Harden Cloud Environments: Mandate FedRAMP-certified cloud environments for AI workloads, conducting regular penetration testing.
Ensure your cloud services meet FedRAMP requirements.
Emulate federal government cloud security controls, even if you're not a federal agency.
Continuous Vigilance: Monitoring for Vulnerabilities and Bias: Automate AI model updates and security patches, leveraging threat intelligence feeds to pinpoint AI-related vulnerabilities.
Conduct continuous AI vulnerability testing for bias, adversarial manipulation, and exploitability.
Data Privacy is Paramount: Encrypt all AI-handled sensitive data sets, vigilantly monitoring AI systems for unauthorized data access.
Deploy privacy-enhancing AI models, such as federated learning.
AI-Specific Access Controls and Zero Trust Implementation: Implement robust AI software and supply chain security practices.
Incident Response Planning: Develop comprehensive plans to effectively respond to cyber incidents.
Elevate Secure Software Development Practices: Implement the NIST Special Publication 800-218, Secure Software Development Framework (SSDF) in your software practices.
CIS Controls: Your AI Security Arsenal
Map the CIS Controls framework to the AI security landscape:
Controls 1, 2, 4, and 16 (Software and Supply Chain Security):
Mandate vendors to submit security attestations.
Align AI development with NIST's secure software development framework.
Conduct third-party security assessments.
Control 3 (Continuous Vulnerability Management):
Automate AI model updates and security patches.
Conduct continuous AI vulnerability testing.
Utilize threat intelligence feeds.
Control 5 (Identity and Access Management):
Implement zero trust identity frameworks.
Enforce phishing-resistant MFA.
Limit AI admin privileges using role-based access control (RBAC).
Control 7 (Data Protection and Privacy):
Encrypt all AI-handled sensitive data sets.
Monitor AI systems for unauthorized data access or retention.
Controls 8 and 11 (Secure Cloud and Infrastructure):
Require FedRAMP-certified cloud environments.
Utilize zero trust architecture for networks.
Conduct regular AI system penetration testing in cloud environments.
Control 14 (Secure AI Model Development Monitoring):
Establish secure AI development lifecycle (SAIDL) practices.
Continuously audit AI models for fairness, security, and bias.
Perform adversarial AI testing to detect manipulation threats.
CISOs: Own the AI Security Narrative!
The regulatory landscape is in constant motion. AI security is now a CISO-driven mission, liberated from federal regulation. Proactive security strategies are paramount to your organization's AI future. Stay ahead of the curve, wield the CIS controls, and champion AI resilience.


Once you understand that securing AI Systems is basically covered to 80-90% by a sophisticated (!) cybersecurity program, you recognize: It's no rocket science.