Complexity is Killing Us: Simplifying Cybersecurity for Better Outcomes
Introduction
Hello and welcome to another blog post from CISO Tradecraft, the platform that provides you with the information, knowledge, and wisdom to be a more effective cybersecurity leader. My name is G Mark Hardy, and today, we’re diving deep into the topic of complexity in cybersecurity—why it makes things harder and what we can do to simplify.
Why Complexity Hurts Cybersecurity
A prevailing misconception in cybersecurity is that more complex systems are inherently more secure. However, as British computer scientist Sir Tony Hoare once said, there are two ways of constructing a software design: one is making it so simple that there are obviously no deficiencies, and the other way is making it so complicated that there are no obvious deficiencies. The latter, while seemingly robust, can hide vulnerabilities within its complexities.
Notable Perspectives on Complexity
Tony Hoare: Developed the QuickSort algorithm and received the Turing Award.
Leonardo da Vinci: "Simplicity is the ultimate sophistication."
Einstein: "Everything should be made as simple as possible, but not simpler."
Bruce Schneier: Author of "Data and Goliath," who stated, "Complexity is the worst enemy of security."
These experts remind us that while we keep adding productivity tools for users, we create expanded support problems for IT. Increased complexity also exacerbates the attack surface and reduces visibility into our technology stack.
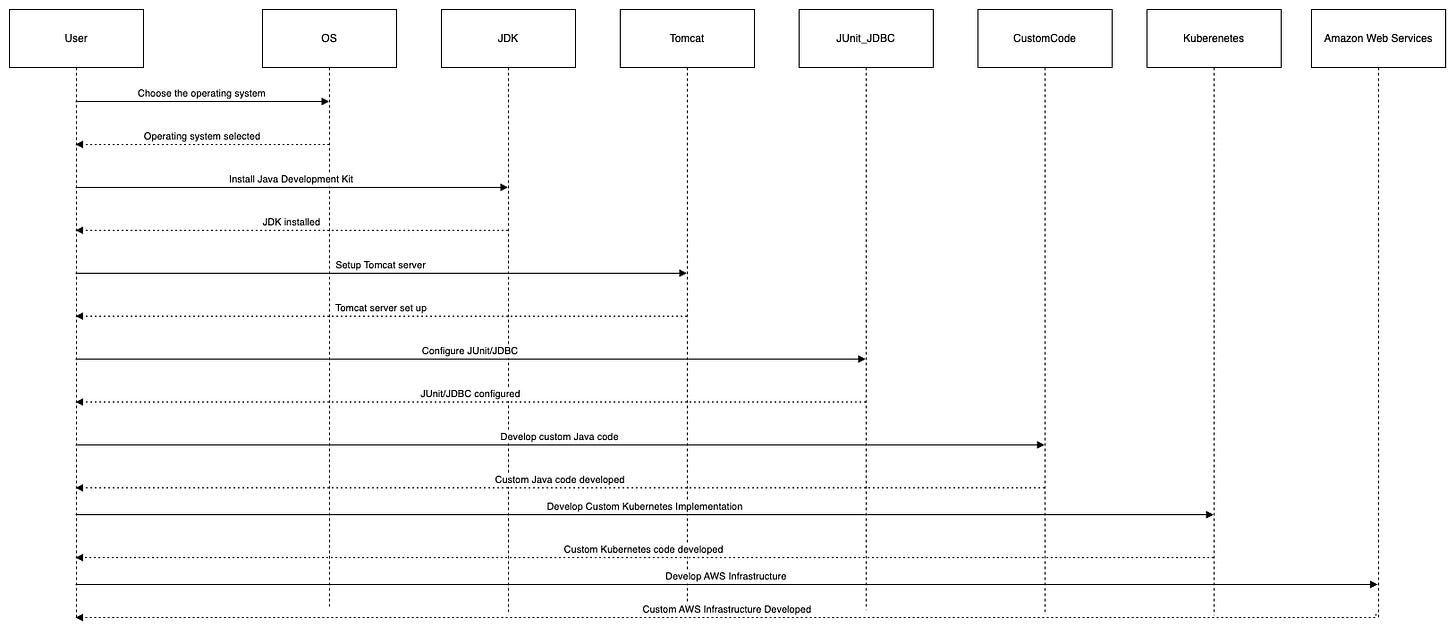
A Simple Example
Imagine a developer tells you they want to build a Java Web Application running on Kubernetes and Amazon Web Services. Here’s a simple illustration of just how many things they need to get correct.
The Hidden Costs of Complexity
There are Four major costs associated with any system:
The cost of Developing (New Features) incurred by Developers
The cost of Developing (Support & Maintenance Costs) incurred by Developers
Licensing Costs
Hosting costs such as Amazon Web Services or On Premises
While we may not fully control control the licensing and hosting aspects, we can plan to build software that optimizes the support and maintenance costs before they become a nightmare.
Steps to Simplify Cybersecurity
Standardize:
Reduce the number of platforms and technologies your organization supports. For example, limiting Java platforms to a few specific versions that have already been blessed by your organization and favoring server-less architectures like AWS Lambda can save time and money while enhancing security.
Minimize:
The less technology you throw into the mix, the fewer components you have to maintain. For instance, using minimalist container images like Alpine Linux over Red Hat can significantly reduce the maintenance burden.
Automate:
Patching and updates should be automated using tools like Puppet, Chef, and Ansible. This not only ensures consistency but also frees up time that can be better spent on strategic initiatives.
Act on Feedback:
Solicit feedback from your developers to identify pain points and complexities. Use this feedback to implement changes that simplify their work processes, making them more efficient and secure.
Understanding the Developer's Perspective
As security leaders, we need to understand that developers are not always equipped with the knowledge to create secure configurations. For example, complexities in setting up a highly available web application on Kubernetes can lead to numerous vulnerabilities. It’s our job to provide the guidance, tools, and processes to make their work easier.
Conclusion
One critical takeaway is that we need to actively minimize technology debt and lower long-term maintenance costs. By implementing the steps above, you can transform your company into a more secure and efficient operation.
Thank you for reading this post on how complexity can hinder cybersecurity efforts. If you found this post helpful, please leave us a comment and share it with others. Remember, simplifying software and technology stacks is key to enhancing security.
Stay safe out there,
CISO Tradecraft®