Don’t Just Spend It: How to Stop Your Cybersecurity Budget From Dying a Million-Dollar Death
Hook: Every Chief Information Security Officer (CISO) faces the same reality: a finite budget, limited staff, and constant pressure to reduce risk. So why, according to expert Ross Young, do most cybersecurity budgets still “go to waste?”. The answer lies in solving the wrong problems, allowing costly organizational clutter to linger, and failing to strategically manage processes and people. Drawing on lessons from Young’s upcoming book, Cybersecurity’s Dirty Secret: Why Most Budgets Go to Waste, we outline actionable recommendations that security leaders can use to unlock their strategic value, maximize outcomes, and prove that they are truly mitigating material threats.
I. Prioritize Smart: Solving the Right Problems with the TaSM
If an organization is focused on solving problems that don’t materially impact the business, they are fundamentally wasting money. The goal isn’t just to spend money; the goal is to solve material threats. Since every organization is unique—a retailer may prioritize high availability around peak sales like Cyber Monday, while a government agency might focus on preventing insider threats, CISOs must tailor their approach.
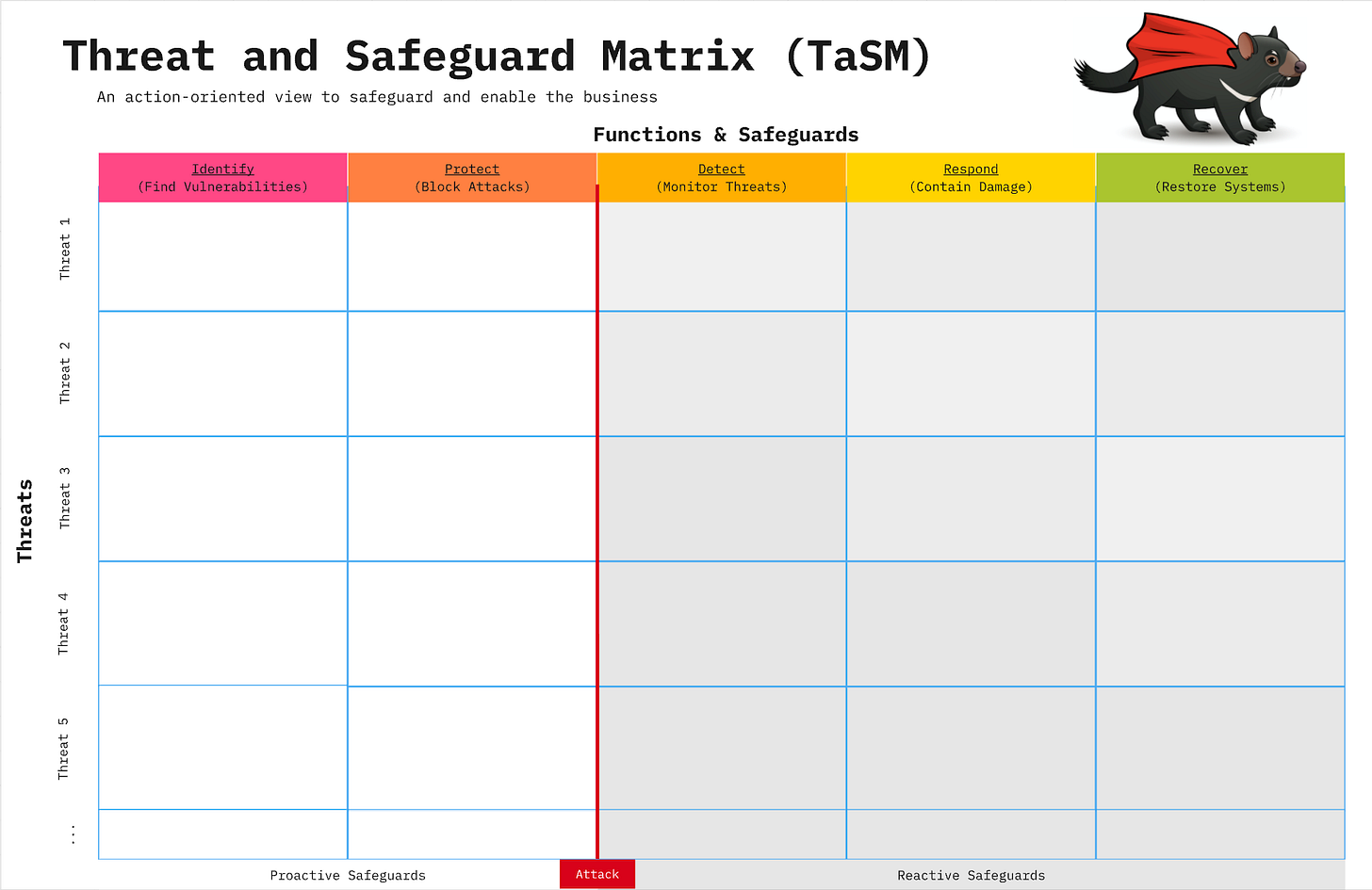
The Power of the OWASP Threat and Safeguard Matrix (TaSM)
To maximize outcomes within a limited budget, security leaders should leverage the OWASP Threat and Safeguard Matrix (TaSM). The TaSM provides a framework for prioritizing and building robust defenses exactly where they are needed—around the most significant threats facing the organization. If security leaders attempt to do everything, they end up with diluted resources, meaning they do nothing well and lack the funding for the best tools needed to safeguard key threats.
The TaSM approach requires scrutiny. When a vendor or internal team proposes a solution, the CISO must ask: “What material threat is this being deployed against?”. Furthermore, where does this solution fit within the core constructs of the NIST cybersecurity framework: Identify, Protect, Detect, Respond, or Recover?.
If a vendor cannot articulate the material risk their solution reduces, the proposed solution might just be a “nice to have,” complete with “bells and whistles” and perhaps even offered with bribes like gift cards or invitations to fancy conference parties. Acquiring a solution that fails to materially reduce risk is, by definition, wasting money.
Actionable TaSM Recommendations:
Consult the DBIR: Every CISO should review the Verizon Data Breach Investigations Report (DBIR) annually to identify the top three attacks. For the current year, these common attacks include phishing, identity-based attacks, and vulnerabilities on unpatched internet-facing systems. Failure to plan for the most common attacks is viewed as negligence.
Look Beyond Compliance: Simply checking compliance boxes does not equate to security. Use your brain. For instance, if an organization uses entirely Commercial Off-the-Shelf (COTS) or SaaS software and writes no internal code, extensive compliance requirements for a DevSecOps shop are irrelevant; focus should be shifted to important areas.
Anticipate Future Risks: While the DBIR is useful, it is “time late”. CISOs must crystal ball future problems, such as those related to Artificial Intelligence (AI). The TaSM framework can be applied to anticipate AI risks, such as leaks (people uploading proprietary data), failure to meet due care standards, or models grabbing databases.
Define Vague Threats: Avoid broad, vague goals like “stop AI threats.” Instead, define specific risks: “Are we trying to stop people uploading sensitive data to ChatGPT, or stop our chatbots from hallucinating?” These require very different solutions and safeguards.
Measure Progress: Implement “metrics that matter”. Once risks are identified, track progress monthly to determine if the organization is getting better, worse, or staying the same in its ability to stop those material threats.
II. Cutting the Clutter: The Murder Board and Effective Protection
A frequent and costly mistake for a CISO stepping into a new role is adopting a “rip and replace” mentality. They see 50-80 existing tools and decide to standardize on tools they were familiar with from their previous organization (e.g., swapping Vendor X for CrowdStrike). This increases the budget substantially, requiring the acquisition of 5-10 new tools, months of running parallel operations, and additional staffing—all requiring begging the CFO for more money.
The better approach is the Murder Board exercise. This systematic review helps reduce existing waste first, freeing up internal capital to acquire desired tools strategically.
The Murder Board Protocol:
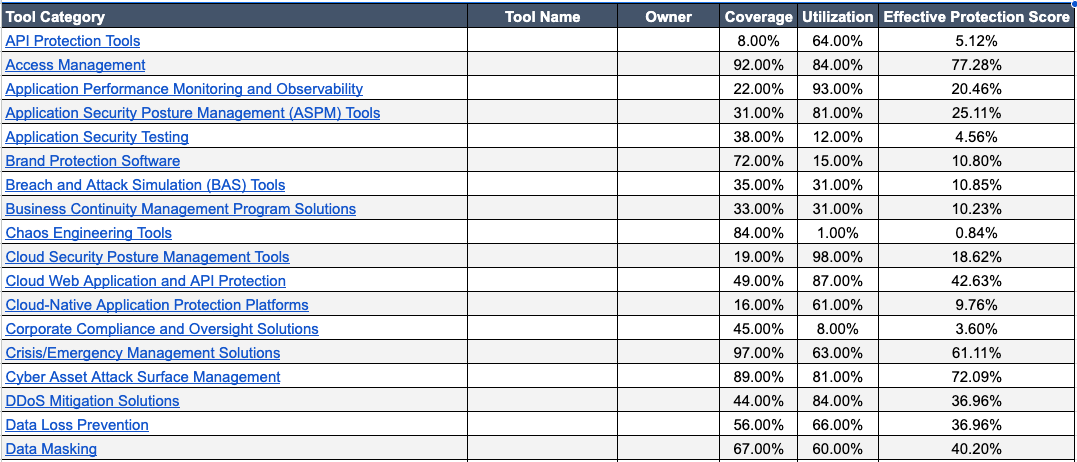
List the 50+ security tools currently deployed and scrutinize their real-world value across four key dimensions:
Deployment Coverage: What percentage of servers or endpoints is the tool actually deployed on? If the deployment is not 100%, the organization is “flying blind” and coverage is diluted.
Feature Effectiveness (Vaporware): Are all key features turned on? Often, features are disabled because they generate too many alerts for the Security Operations Center (SOC). If the features are off, the organization has deployed “vaporware”—software that exists but doesn’t function as intended. For example, an organization may claim to have rolled out a Web Application Firewall (WAF), but if the developers turned off all the rules because they were impacting the website, the WAF is worthless.
Telemetry and Reporting: How many machines have actually “beaconed back to the portal” in the last 30 days?. An agent might be installed but turned off or blocked by a firewall rule, significantly diluting the true visibility and coverage.
Real-World Value and Redundancy: How many real attacks did the tool stop last year?. Even more critically: was it the only tool in your arsenal that could stop that attack?. If three different tools provide redundant coverage for the same attack, money is being wasted, and simplification with a single effective tool is possible.
By taking this rigorous murder board approach, CISOs can often identify three to five diluted tools that provide little value and eliminate them, saving millions. This freed-up money can then be redirected to acquire the five tools the CISO truly needs, without having to request additional funding from the CFO.
Effective Protection and Prudent Practice:
The Murder Board exercise directly helps calculate the “effective protection score,” which asks how effective a tool is at keeping the organization secure. This evaluation also involves looking beyond just attacks stopped in the last 12 months. Sometimes, a tool didn’t stop an attack simply because the specific attack didn’t occur. This is where prudent business practice comes in.
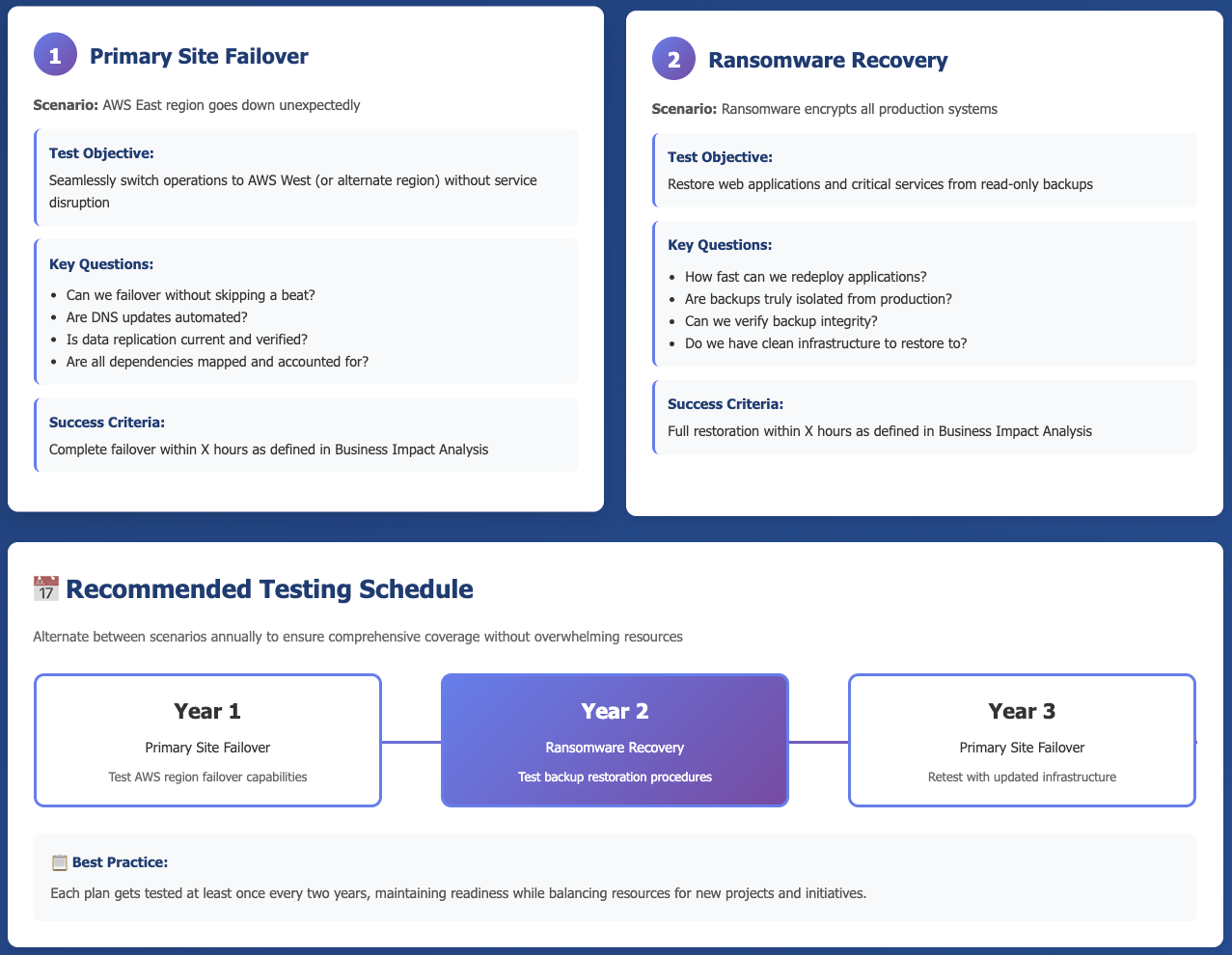
A CISO should consider the low-probability, high-impact events. For instance, having resiliency plans to shift off a specific mail provider when an AWS region (like US East 1) goes down, even if this hasn’t happened recently, is a critical safeguard. CISOs should ensure such resiliency plans are tested and that configurations (like DNS Time to Live) are optimized for agility, not just bandwidth savings.
III. Strategic Leadership: Beyond the Technical
A CISO’s tenure is defined not just by tools but by strategic leadership, especially in the first 90 to 180 days.
Avoiding Leadership Blunders
If a new CISO starts ripping out existing tools that are working, merely based on personal preference, they send a damaging message: “You guys are all stupid. You’re choosing the wrong tools. You guys suck. Go fix it.”. This approach severely damages rapport and trust within the first 90 days.
When inheriting a team, the CISO must stop, look, and listen. If the previous leader was poor but the team is performing well, they likely mastered their existing tools and learned to ignore their boss. In this case, the new CISO should become a “learner” and run to the head of the team that is already moving in the right direction. If the previous boss was good and the performance is excellent, the CISO should simply go get a cup of coffee and act as an agent to get the high-performing team whatever resources they need.
A CISO must avoid the temptation to assume that every problem looks like the one solution they are most comfortable with. Instead, they must use diagnostic tools, like the TaSM, to match the organization’s material threats to its existing solution sets.
IV. Negotiate Smart: Mastering Contract Agreements
Master Service Agreements (MSAs) are often the most challenging and lengthy part of procurement, sometimes taking a year due to large company bureaucracy. While getting funding may be easy with a compelling argument, procurement can be fraught with delays.
Key Contract Negotiation Tips:
Demand a Capped Uplift: CISOs must proactively push for contract clauses that limit price increases upon renewal (the “uplift”). Forcing a cap, such as 3%, prevents vendors from “gouging” the company (jumping up 50% in price) once the organization has spent significant time and resources deploying the tooling. A cap ensures that increases align reasonably with inflation.
Rethink Liability Limits: Legal departments often demand unlimited liability from vendors, but this is highly impractical. Most vendors will cap liability, perhaps at three times the contract price. CISOs should discuss realistic settlement terms with procurement beforehand.
Consider Self-Insuring: Instead of allowing vendors to embed insurance costs with a markup into 50 different contracts, it may be a smarter business practice for the organization to self-insure across all vendors. This avoids paying 50 different markups and can save significant money.
Make it Mutually Incentivized: Negotiation works best when incentives are mutual. If you control the format (like writing the Non-Disclosure Agreement or setting the contract terms), you guide the negotiation toward the middle ground.
V. Eliminating Toil: The Cheaper, Faster, Better Approach
The old consulting rule was to “pick any two” of better, faster, or cheaper. However, CISOs can achieve all three by systematically reducing the toil of operations and maintenance. This involves applying mature engineering methodologies like Lean Process Improvement and Six Sigma to bureaucratic security operations.
Process Improvement Case Study: Vulnerability Management
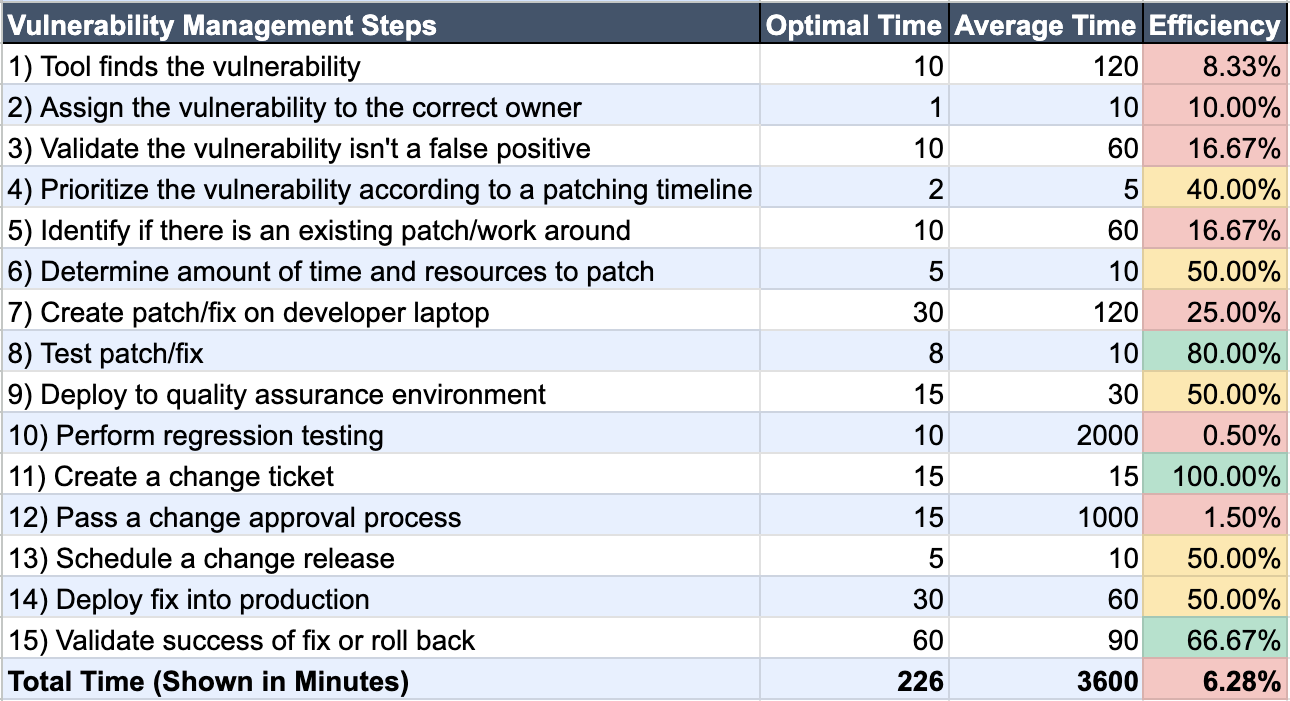
One organization used this approach to reduce its mean time for patching from over 300 days to under 30 days—a spectacular, ten-fold improvement.
The steps taken:
Map the Process: Break the entire vulnerability management process into 10 to 15 distinct steps (e.g., scanning, identifying the owner, finding the fix, gaining approval).
Measure the Wait: Measure the time each step takes (minutes or days).
Identify Bottlenecks: Assemble a council of the organization’s “smartest people” (from network, apps, server, and database teams). Challenge them to totally blow away the existing process and build one from scratch, identifying opportunities to save time.
Eliminate Friction: Bottlenecks often appear as huge wait cycles. For instance, a weekly change approval board might cause enormous delays. By converting that step into a modern, automated system (like a GitHub approval process), a process that took a week can be reduced to a couple of hours.
Achieve Lasting Change: By fixing just two out of 15 subprocesses, the organization saved 80% of the time required for patching, leaving a lasting, positive impression on the organization.
The Win-Win Scenario: CI/CD Pipeline
Process improvement creates a win-win scenario across the business:
When a CISO helps replace an insecure, vulnerable system (like an old Jenkins infrastructure) with a modern, serverless CI/CD pipeline, the development team gets a better system, and security eliminates vulnerabilities.
The previous system might have required 80% of the team’s time (8 out of 10 people) just for operations and maintenance (O&M). The new 2.0 version reduces O&M to 10%.
The CISO can then tell the CFO that the project cost $2 million but will save $1.4 million annually by converting maintenance hours into headcount dedicated to new business initiatives.
This approach helps the CISO build credibility with IT and developers, who often view security as a roadblock, by demonstrating that security is actually there to make their lives “cheaper, faster, better”.
VI. Investing in People: Reducing Human Cost Waste
Waste is not limited to software; human cost waste occurs through low loyalty, poor retention, and disengagement. CISOs must focus on ensuring employees feel included and engaged in the decision-making process.
Tools for Alignment and Retention:
Personal Values Exercise: This tool helps managers understand employee motivation. Team members rank the 50 things they value most in the workplace (e.g., adventure, high pay, work-life balance, or work-life balance). Managers can then use this ranking to coach and mentor staff effectively, tailoring management style based on whether an employee values “high pay and excitement” versus “lifestyle balance and work from home”.
Roses, Thorns, and Buds Exercise: This is the easiest, cheapest exercise available, requiring only a stack of post-it notes. Ask the team to identify three ideas for each category:
Roses: What is working well? (These must not be screwed up).
Thorns: What is not working? (The bad things that require fixing).
Buds: What new ideas should the team try?.
Championing Ideas: By collecting the team’s collective feedback (e.g., 30 ideas per column from 10 people) and summarizing the emerging themes, the manager can prioritize fixes and new initiatives. When the manager champions these team-generated ideas, employees are highly bought in and view the workplace as inclusive. When people own part of a decision, they are motivated to defend and support it.
By focusing resources strategically using the TaSM, ruthlessly eliminating diluted tools via the murder board, applying process improvement techniques like Lean and Six Sigma, and fostering an inclusive environment through people-centric exercises, CISOs can convert their limited budgets into maximum security outcomes.
This post draws extensive insights from the CISO Tradecraft podcast discussion (Episodes 255 & 256) with Ross Young, author of the upcoming book, Cybersecurity’s Dirty Secret: Why Most Budgets Go to Waste. If you like this content please check out the Ross’s course, “Master the Budget Game in Cybersecurity.”