From Stagnation to Superpower: Reimagining the World-Class SOC – A CISO's Playbook for the Future
Remember when 11 Strategies of a World-Class Cybersecurity Operations Center hit the shelves (or, more accurately, the free PDF download)? It quickly became a foundational text for anyone looking to build or run a Security Operations Center (SOC). But in the fast-evolving world of cybersecurity, what happens next? The landscape is shifting, new threats emerge daily, and our teams face unprecedented pressures. We recently sat down with author Carson Zimmerman, a veteran in cybersecurity and security operations, to delve into the future of SOCs, discussing everything from fighting burnout to embracing AI and neurodiversity. His insights offer a critical roadmap for CISOs looking to future-proof their operations.
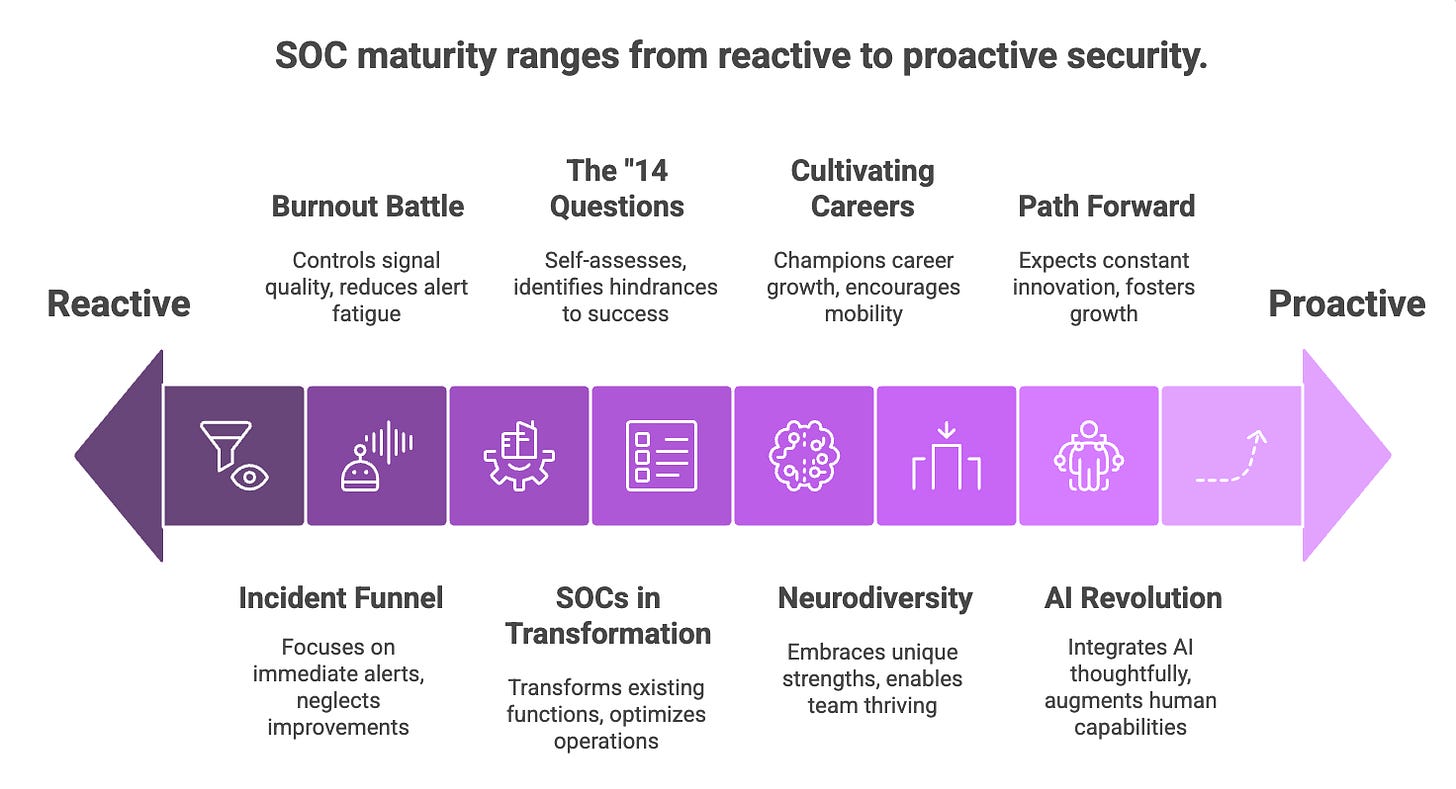
Beyond the Incident Funnel: Fighting Stagnation
For many in a SOC, the daily grind involves a constant struggle between responding to incidents (detect, investigate, respond, recover) and finding time for strategic improvements. This "turning the crank" can lead to a profound sense of stagnation, where teams are so focused on the immediate alerts that they neglect vital investments in getting better. This isn't just about efficiency; it's about team morale and long-term effectiveness.
Carson Zimmerman advocates for treating these investment areas as "first-class citizens," dedicating time to them even during "normal" operations, as if they were as critical as the incident funnel itself. This could involve engaging deeply with service owners for co-hunting initiatives, collaborative detection creation, or meticulously developing and refining Standard Operating Procedures (SOPs) and playbooks. Crucially, it means using every incident as a training venue and a Post-Incident Review (PIR) opportunity to identify areas for improvement. Building clear metrics and rhythms around these improvement activities not only boosts engagement and investment by the workforce but also proactively creates capacity for when major incidents inevitably hit. When a significant breach occurs, these improvement activities can be temporarily paused, but it’s vital to resume them quickly to avoid getting stuck in a perpetual incident response mode.
CISO Recommendation: Prioritize Proactive Improvement. Mandate dedicated time for "getting better" activities within your SOC's operational rhythm. This isn't optional; it's a strategic imperative. Implement metrics that track progress in areas like playbook development, co-hunting sessions, and post-incident learning, alongside traditional incident response metrics. Foster a culture where every incident, regardless of size, is viewed as a valuable training ground and an opportunity to refine processes and tools. This proactive investment will build resilience and prevent burnout by giving your team a sense of progress beyond just clearing alerts.
The Burnout Battle: Tuning the Signal
One of the biggest, if not the biggest, contributors to SOC burnout is the sheer volume of alerts. Many SOCs fall into a common trap: simply turning on off-the-shelf security products with default settings, which inevitably leads to a flood of unmanageable, noisy alerts. This deluge creates what's known as "alarm fatigue," overwhelming analysts and diminishing their ability to identify genuine threats.
Zimmerman emphasizes that controlling the signal coming into the SOC – the quality and relevance of alerts – is arguably the number one investment area for reducing burnout. It's not a one-time fix but a matter of continuous "discipline" that requires a consistent, day-over-day, week-over-week investment in "tuning". The goal, which every security vendor now discusses, is to reduce alarm fatigue and improve situational awareness, allowing analysts to focus on what truly matters. This tuning process is continuous, adapting as your environment and threat landscape evolve.
CISO Recommendation: Invest Relentlessly in Signal Quality. Make alert tuning and suppression a top-tier operational priority. Empower your SOC analysts to actively flag noisy or low-value alerts, and dedicate specific resources (whether people or time) to investigate and address the root cause of these alerts, rather than simply processing them. Establish clear Service Level Agreements (SLAs) or objectives around alert reduction and accuracy. Regularly review alert efficacy with your team to ensure they are getting the high-fidelity signals they need to be effective and to prevent the overwhelming feeling that leads to burnout.
SOCs in Transformation: Not Starting From Scratch
While the idea of building a brand new SOC from the ground up might sound appealing – like being part of a "pre-commissioning crew" for a ship – it's a rare experience today. With widespread digital transformation, most organizations already have some form of digital footprint and existing security functions, however nascent or fragmented. Instead of creating a SOC from nothing, organizations are typically undergoing a "transformation" – insourcing or outsourcing existing functions, or mixing approaches to optimize their operations. Often, a major incident acts as a powerful catalyst for a necessary change in investment or strategy, forcing a re-evaluation of existing "hodgepodge" solutions.
CISO Recommendation: Embrace the Transformation Mindset. Recognize that your SOC journey is likely one of continuous transformation, not a clean slate. Conduct regular, honest assessments of your current security operations capabilities, identifying what's working, what's not, and where improvements can be made, whether through insourcing, outsourcing, or a hybrid model. Leverage any major security incidents as a strategic opportunity to secure increased investment and executive buy-in for long-term improvements, moving beyond short-term fixes to truly overhaul your operational model.
The "14 Questions": A Simpler Path to Success
Recognizing the complexity and time investment of comprehensive maturity frameworks like SOC-CMM or ENISA's CERT maturity model, Zimmerman developed a simpler, more direct approach: the "14 Questions." These are the most critical questions a SOC needs to ask itself to swiftly identify what's hindering its success and where attention is most needed.
For example, asking "how long has a given group of people or a given role in a SOC done the same thing in the same way?" can reveal deep-seated stagnation if the answer is "years." This highlights a lack of evolution in processes and roles, which is critical in a dynamic field like cybersecurity. Another key question involves measuring the time it takes to get engineering support for a SOC's needs, from the initial request to actual operational impact. If this "time to ops impact" is excessive, it points to a significant bottleneck. Zimmerman also highlights the power of "anecdata" (anecdotal data) over complex dashboards for communicating issues to executives, as a compelling story or vignette can often be just as effective in demonstrating a problem (e.g., "it takes me three hours to triage every alert, and we have 10,000 a day") and securing buy-in as six months of metric-building.
CISO Recommendation: Adopt a Pragmatic Self-Assessment. Regularly engage your SOC leadership and teams in a frank discussion using "The 14 Questions" (or similar critical self-assessment questions). Encourage open, honest answers, and use these discussions to pinpoint areas of stagnation or inefficiency. Don't shy away from "anecdata" when communicating challenges and successes to senior leadership or budget holders. A powerful, relatable story about operational struggles can often resonate more deeply and secure resources faster than intricate data visualizations. Ensure your SOC has dedicated, responsive engineering support, ideally integrated directly or with streamlined processes to address their needs rapidly, reducing time to operational impact.
Neurodiversity: A SOC Superpower
The cybersecurity field, and SOCs in particular, are increasingly recognizing the unique strengths that neurodiverse individuals bring. While historically the field might have seemed "unilateral" with a predominantly homogenous demographic, it has diversified greatly, with specialists emerging in various areas from GRC to malware analysis and cloud authentication. A SOC is not a monolithic entity; it's made up of diverse "personas" – from triage analysts and incident responders to hunters, malware analysts, and data scientists.
As Zimmerman points out, the person best suited to "herding 50 cats" during an incident call is likely not the same person you'd want doing detailed PE header analysis. Neurodiversity, including conditions like ADHD, autism spectrum, and anxiety, can manifest as true "superpowers" in these specialized roles. The ability to hyperfocus on a complex problem, or to see intricate connections and bring together disparate data points that others might miss, are invaluable assets in a SOC. Leaders have the unique challenge and privilege of recognizing and embracing these superpowers to enable their teams to thrive and proactively prevent major incidents.
CISO Recommendation: Actively Embrace Neurodiversity. Foster an inclusive culture within your SOC that not only accepts but actively celebrates neurodiversity. Understand that different security roles benefit from different cognitive strengths. Educate your leaders and managers on how to identify and leverage these "superpowers" (e.g., hyperfocus, pattern recognition, deep analytical ability) to place individuals in roles where they can truly excel. Create an environment where diverse perspectives are valued, and problem-solving approaches are encouraged, recognizing that unique ways of thinking can lead to breakthroughs in threat detection and response.
Cultivating Careers in a Dynamic Field
Cybersecurity is a "dynamic field" that necessitates constant career and skills progression. Unlike some fields that might promote an "up or out" model, or keep technical experts in the same role for decades, the SOC environment demands continuous movement and growth. Leaders play a crucial role in identifying talent, believing in their people, and pushing them into new challenges where they can grow, even if it means "push[ing] them into the deep end and watch them succeed."
People who have experience in areas like penetration testing, for example, often make some of the best SOC professionals because they understand the adversary's mindset. The key is to ensure that all roles within the SOC are progressing and that people are given opportunities for internal career development, or even movement in and out of the SOC itself. This means resisting the "gray-haired major" trap where highly skilled individuals are kept in static roles, despite their brilliance. Instead, cultivate a culture where lateral moves, cross-training, and external experiences (like red teaming) are encouraged, enriching the entire team's capabilities.
CISO Recommendation: Champion Career Growth and Mobility. Develop transparent and flexible career progression paths within your SOC. Actively identify high-potential individuals and provide them with challenging assignments and mentorship to foster their growth. Encourage both vertical and horizontal movement within the security team, and even consider rotations in and out of the SOC (e.g., to red teaming, GRC, or engineering roles) to broaden expertise. Advocate for the value of specialized technical roles to HR, ensuring that individuals who excel as "rockstars" in technical positions are recognized and rewarded, even if their career path doesn't follow a traditional management ladder.
The AI Revolution: Thoughtful Insertion, Not Replacement
The buzz around Artificial Intelligence (AI), particularly large language models (LLMs) and generative capabilities, is undeniable. While many startups and major companies are pouring resources into this area, the vision of AI replacing human tasks needs a dose of reality. Zimmerman argues against the misconception that SOC work is static or finite; there's always more signal to consume, analyze, and respond to. The focus should be on what tasks can be automated, allowing humans to shift to other, higher-value activities, rather than aiming for a "human body count down to zero."
While areas like code summarization and alert triage are immediate targets for AI, it's crucial to think about how generative AI can empower all SOC personas across the incident lifecycle. Drawing parallels to network intrusion prevention systems (IPS) and Security Orchestration, Automation, and Response (SOAR) technologies, Zimmerman stresses the importance of "tuning" AI implementations. Just as IPS systems needed to be run in "alert only" mode and carefully tuned before going "full auto," AI in the SOC requires careful configuration and transparent understanding of how models operate. Adversaries will undoubtedly use AI to move faster and with greater intensity, so SOCs must incorporate it to keep pace. However, "thoughtful insertion" is key. Starting now is advisable, focusing on pragmatic application, clear measurements of success, and remembering that traditional automation techniques like Python scripts still hold significant value.
CISO Recommendation: Strategically Integrate AI with Human Oversight. Begin pragmatic experimentation with AI and generative models within your SOC now, if you haven't already. Focus on "thoughtful insertion" that augments human capabilities rather than attempting full replacement. Start with tasks like code summarization, initial alert triage, and data correlation, but explore how AI can empower all SOC personas across the entire incident lifecycle. Emulate the "alert-only" then "full auto" model from IPS: deploy AI tools in monitoring or auditing mode first to tune them and build trust before enabling automated actions. Establish clear, measurable success metrics for AI implementations (e.g., time savings, alert accuracy, reduction in false positives). Remember that tried-and-true automation methods like Python scripting remain valuable and should not be overlooked in the pursuit of shiny new tech. Understand that adversaries are leveraging AI, so incorporating it into your defensive strategy is essential for competitive advantage.
The Path Forward: Continuous Improvement is the Only Constant
The overarching message for SOC leaders and CISOs is simple yet profound: "expect constant and continual improvement and innovation from your SOC." If your current operational model or resourcing doesn't support this continuous evolution, it's time to re-evaluate fundamentally. The goal is to empower your SOC to either reduce low-value work or refocus resources on activities that foster continuous improvement and growth, ensuring your team is always getting better at what they do.
The future of the SOC isn't about standing still; it's about evolving, adapting, and embracing new approaches to security operations. By prioritizing strategic investments, nurturing talent, and thoughtfully integrating emerging technologies, CISOs can transform their SOCs from reactive incident centers into proactive powerhouses capable of navigating the complex cybersecurity landscape of tomorrow.