Introduction:
In today's constantly evolving threat landscape, it is crucial for organizations to regularly update their cybersecurity approach to stay ahead of potential risks. Join us as we explore the steps you can take to ensure your cybersecurity strategy is robust and effective.
I. Assessing Your Current State
Before embarking on the journey of refreshing your cybersecurity strategy, it is essential to understand your organization's current state. This includes evaluating your people, processes, and tools to identify any gaps or areas of improvement. By performing a comprehensive assessment, you can establish the ground truth of your cybersecurity posture.
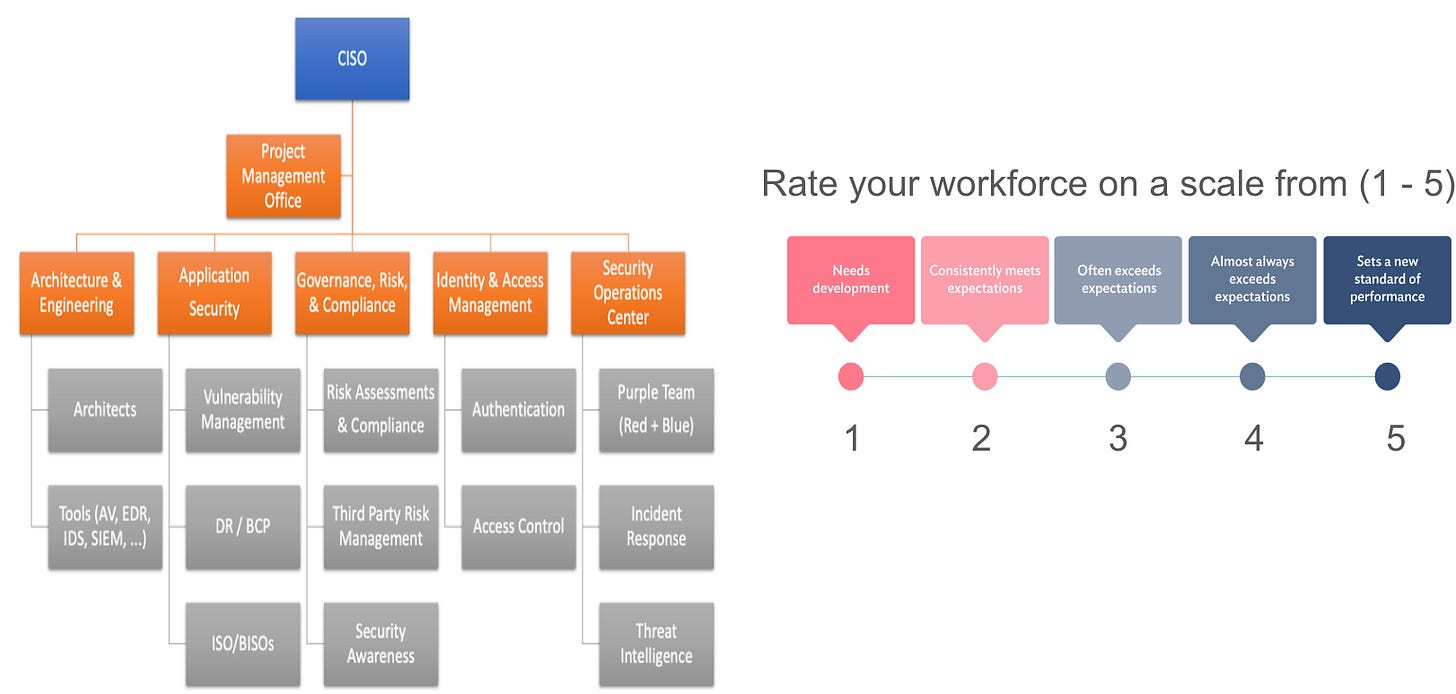
A. People - Workforce Maturity Assessment:
Start by analyzing your workforce structure and capabilities. Evaluate your cyber teams and their sub-functions, rating their performance on a scale from one to five. This assessment helps identify any dysfunctional structures, ineffective team members, or unclear responsibilities within the organization. By pinpointing these gaps, you can address them through upskilling, recruitment, or replacing underperforming individuals.
B. Process - Cybersecurity Controls Validation:
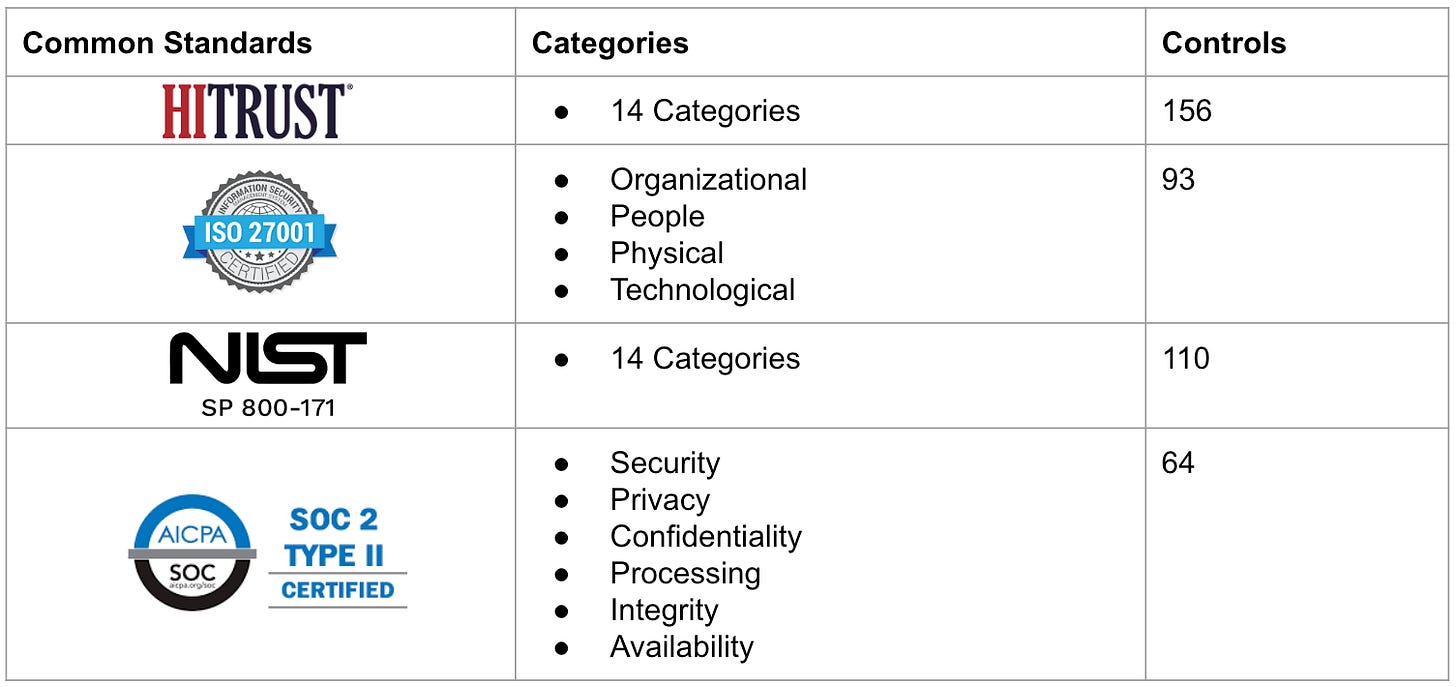
Outsourcing an external audit can provide a clear picture of your organization's adherence to security controls and best practices. Engage an auditing organization to perform assessments such as SOC 2 Type 2, ISO 27001, HITRUST, or CMMC (for organizations working with the Department of Defense). This external audit enables you to receive unbiased feedback on your security controls' effectiveness and demonstrates your commitment to cybersecurity to your board and executive leadership team.
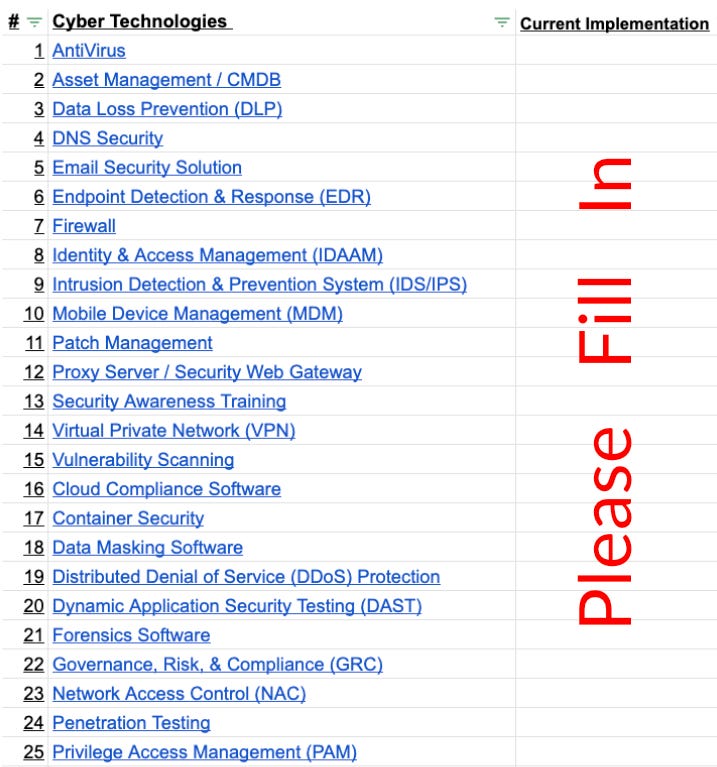
C. Tools - Catalog of Cybersecurity Tools:
Create a comprehensive catalog of the cybersecurity tools being utilized within your organization. Identify any underutilized tools and their potential for additional value. Uncover any configurations or features that could enhance your organization's security posture without requiring additional investments. By organizing these tools into categories, you can identify any critical tooling gaps and evaluate their impact on your overall risk profile. Note there’s more than 25 security tools.
II. Defining Your Desired Future State
After assessing your current state, it is crucial to define your desired future state for a successful cybersecurity strategy refresh. Align your objectives with your organization's business goals, relevant laws and regulations, and applicable cybersecurity frameworks.
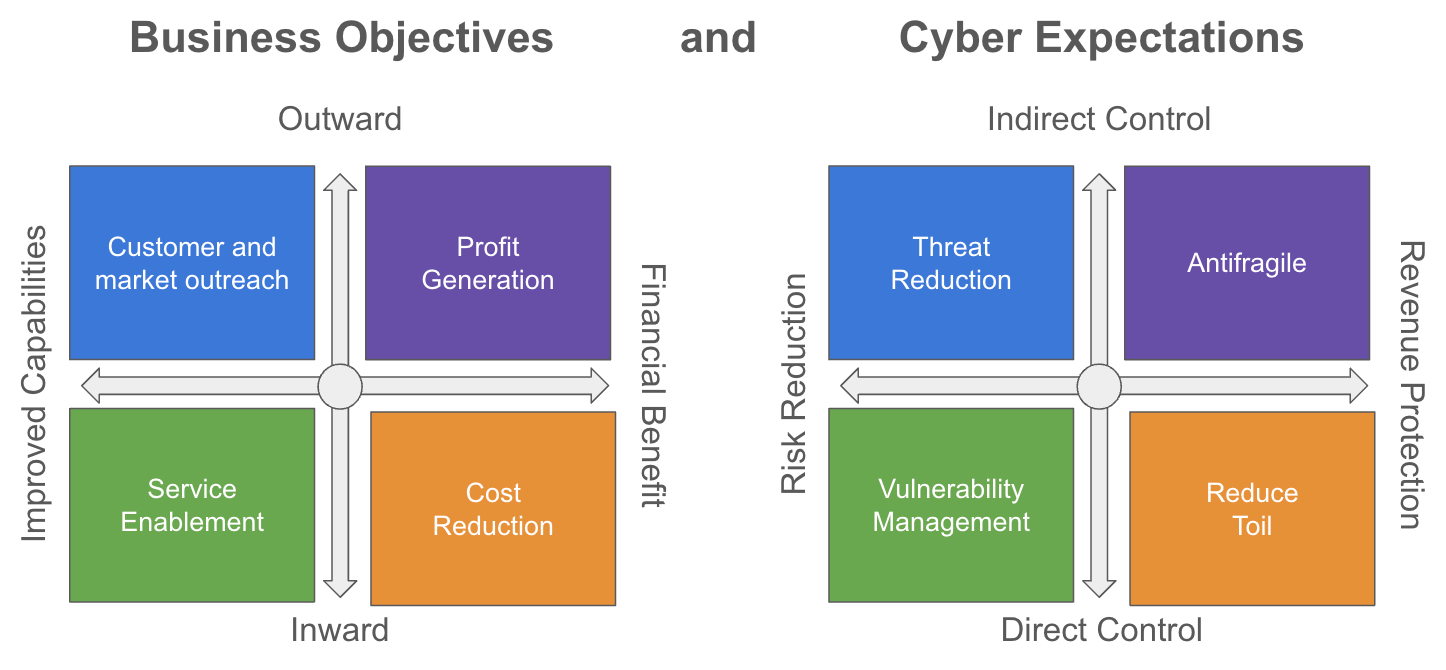
1. Business Requirements Analysis:
Understand your organization's business objectives and align them with your cybersecurity strategy. By collaborating with management, you can identify long-term growth objectives, service enhancements, and cost reduction opportunities that require secure implementation. Example: If the business wants to reduce cost, then cyber should look at how it can reduce toil to developers.
Additionally, liaise with compliance and legal teams to determine the regulations and standards applicable to your organization (e.g., PCI DSS, HIPAA, GDPR). Then map that into how you can collect evidence for specific applications.
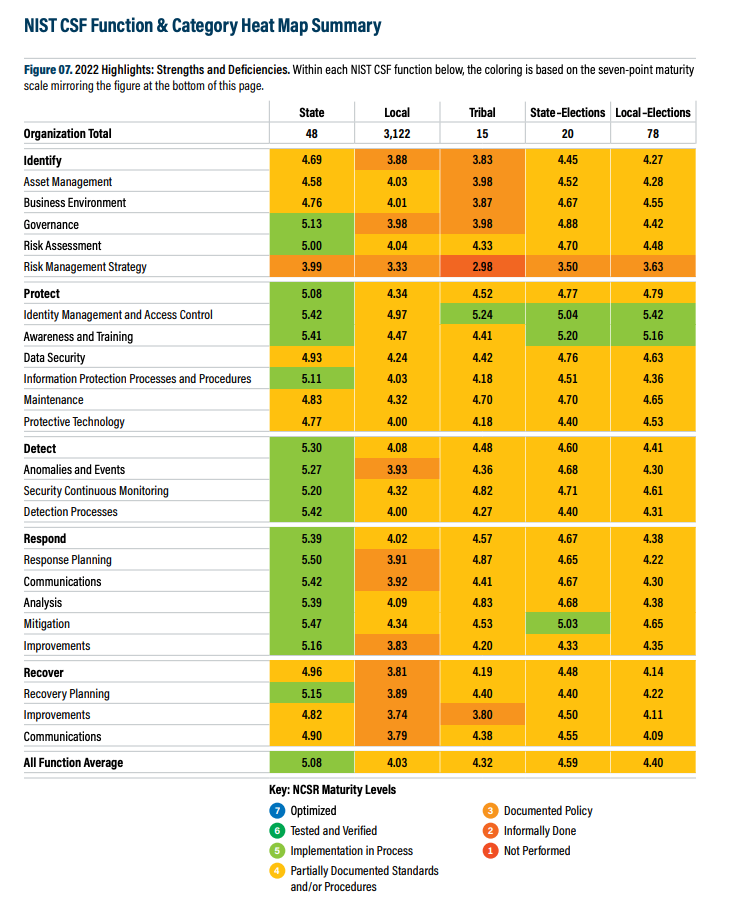
Mapping your cyber program to established frameworks such as NIST Cybersecurity Framework or ISO 27001 will provide focal points for improvement and maturity enhancement. For example: The Nationwide Cybersecurity Review ranked each government agency on a scale of 1-7 for each NIST category.
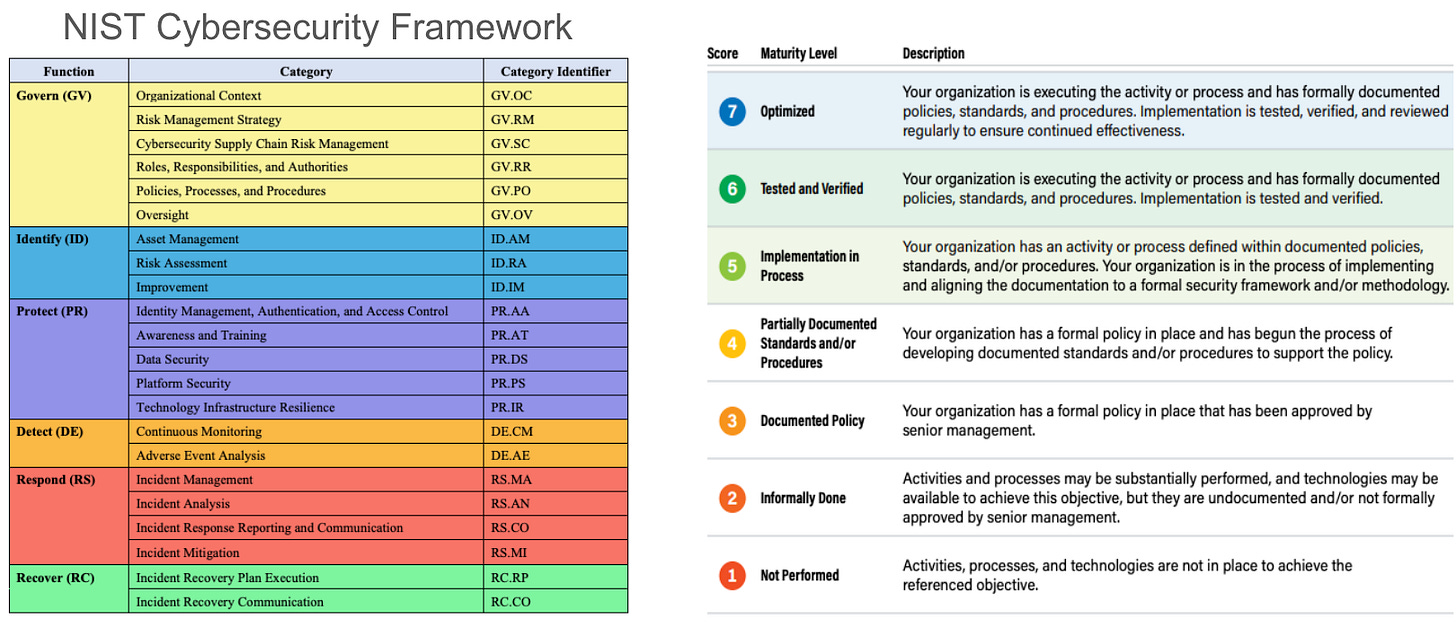
Note here is an updated view that you could use to score each Category in NIST 2.0
2. Defining Future State Objectives:
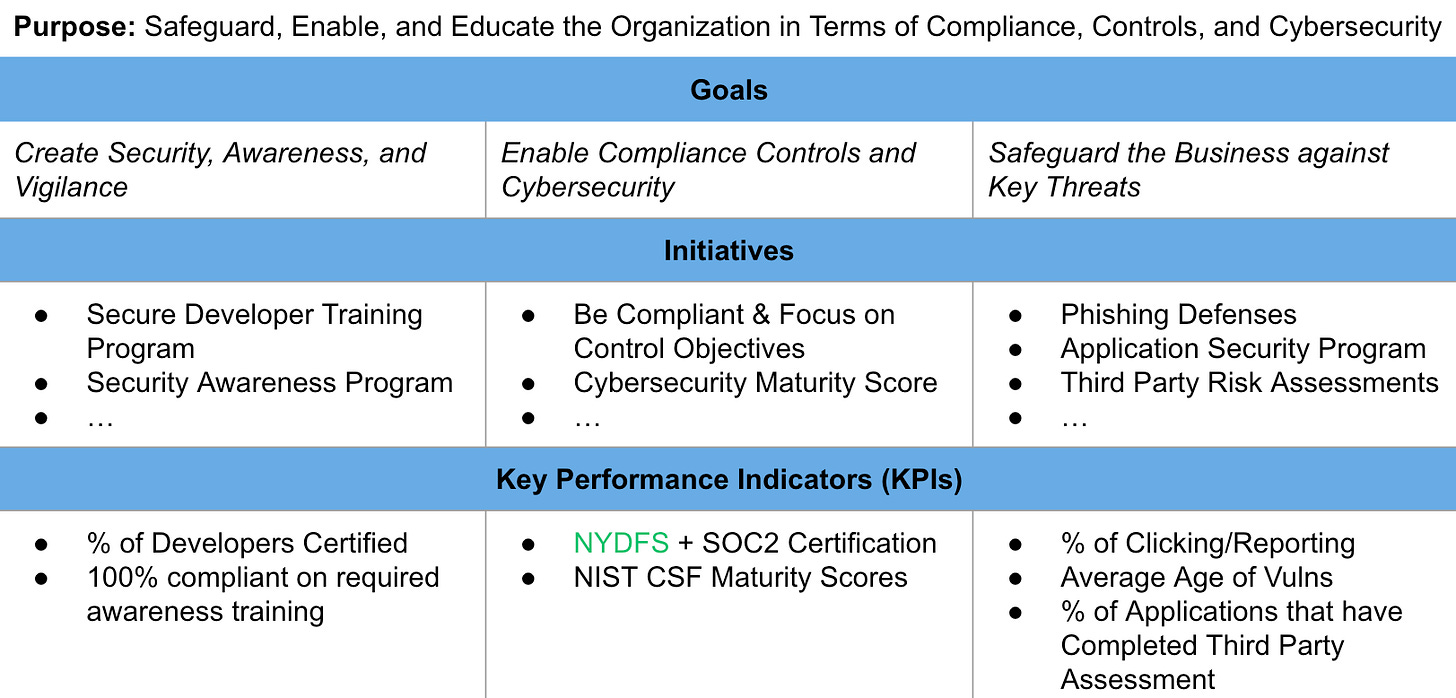
Based on the analysis of business requirements and applicable frameworks, establish concrete objectives for your cybersecurity strategy. These objectives should focus on creating a security vigilant organization, maintaining compliance with relevant controls and regulations, and safeguarding the business against key cybersecurity threats. Each objective should be specific, measurable, achievable, relevant, and time-bound (SMART).
III. Bridging the Gap: Creating a Roadmap
With a clear understanding of your current state and desired future state, it is time to bridge the gap and create a roadmap for success. This roadmap will outline the actions and initiatives required to achieve your cybersecurity objectives.
1. Gap Analysis:
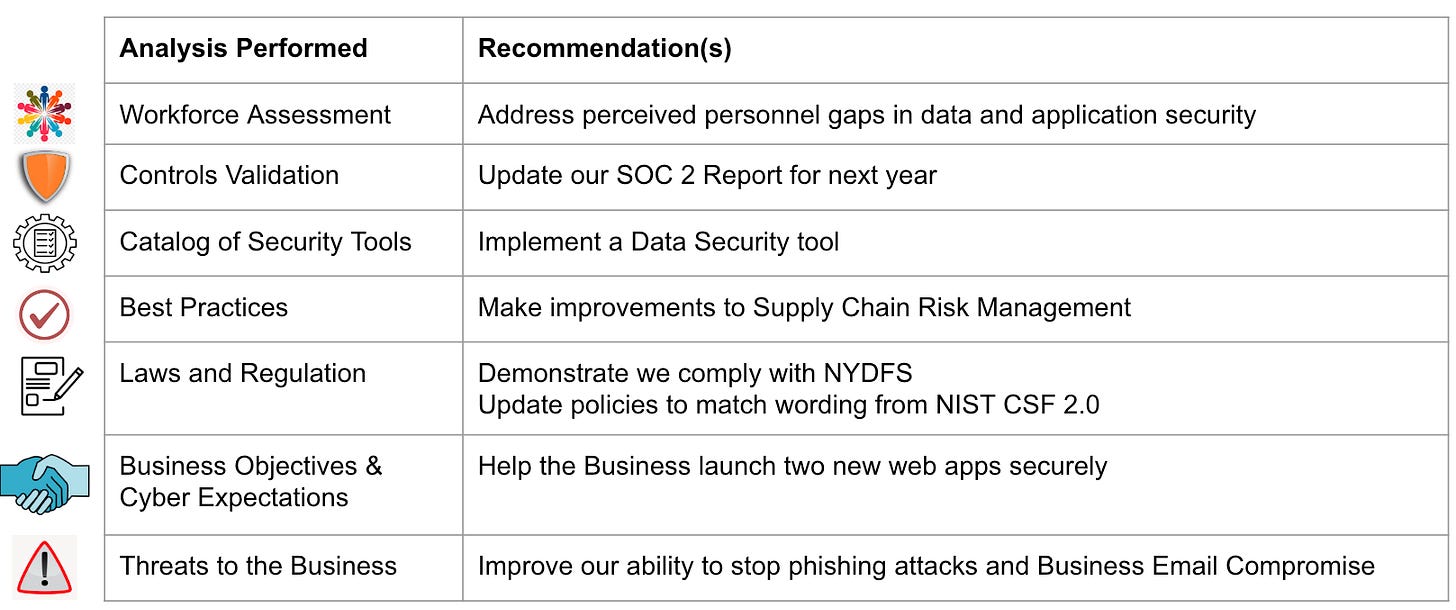
Perform a gap analysis to identify the resource gaps needed to reach your desired future state. By quantifying the gaps, you can determine the necessary budget, staffing, and solutions required for success. Identify potential options to address each gap and validate them using a trap analysis exercise, evaluating the best fit and likelihood of success for each option.
2. Initiatives and Key Performance Indicators (KPIs):
Translate your objectives into concrete initiatives and set Key Performance Indicators (KPIs) for each initiative. Initiatives should outline specific actions required to achieve your objectives, such as implementing a secure developer training program, completing compliance reports, or deploying essential security tools. KPIs provide measurable metrics to evaluate the success of each initiative, such as the completion rate of developer training, phishing exercise click rates, or the percentage of endpoints protected by a data security tool. Regularly track and report progress on these KPIs, enabling clear communication to the leadership team on the cybersecurity strategy's effectiveness.
Conclusion:
Refreshing your cybersecurity strategy is essential for staying ahead of evolving threats in the digital landscape. By assessing your current state, defining your desired future state, and creating a roadmap to bridge the gap, you can establish a robust and effective cybersecurity strategy. Regularly reevaluate and adapt your strategy to ensure it aligns with the evolving cybersecurity landscape and supports your organization's business objectives. Remember, cybersecurity is an ongoing journey, and by taking these proactive steps, you can protect your organization from potential risks and enhance your overall security posture.
Thank you for joining us on this journey to refresh your cybersecurity strategy. We hope this guide has provided valuable insights and actionable steps to bolster your organization's security. If you need further assistance or support in implementing these strategies, please don't hesitate to reach out to us at CISO Tradecraft. Stay safe and secure!




Great stuff ! I loved the level of depth you went into for each step