Tired of Talking Tech? The OWASP TaSM is Your Secret Weapon for Cybersecurity Success!
Are you a Chief Information Security Officer (CISO) who feels like you're constantly speaking a different language than your board, your CFO, or even your HR department? Do you struggle to translate complex cyber threats into terms that resonate with the non-technical leaders who control the budget and ultimately define organizational risk tolerance? If your cybersecurity initiatives feel like an endless uphill battle for understanding and resources, then get ready for a game-changer.
Meet Ross Young, a cybersecurity veteran with an impressive background spanning the Central Intelligence Agency (CIA), Capital One, and Caterpillar Financial. Young, who is also authoring a book titled "Cybersecurity's Dirty Secret: Why Most Budgets Go To Waste," developed a powerful framework to help CISOs maximize their cybersecurity spending and fix broken processes.
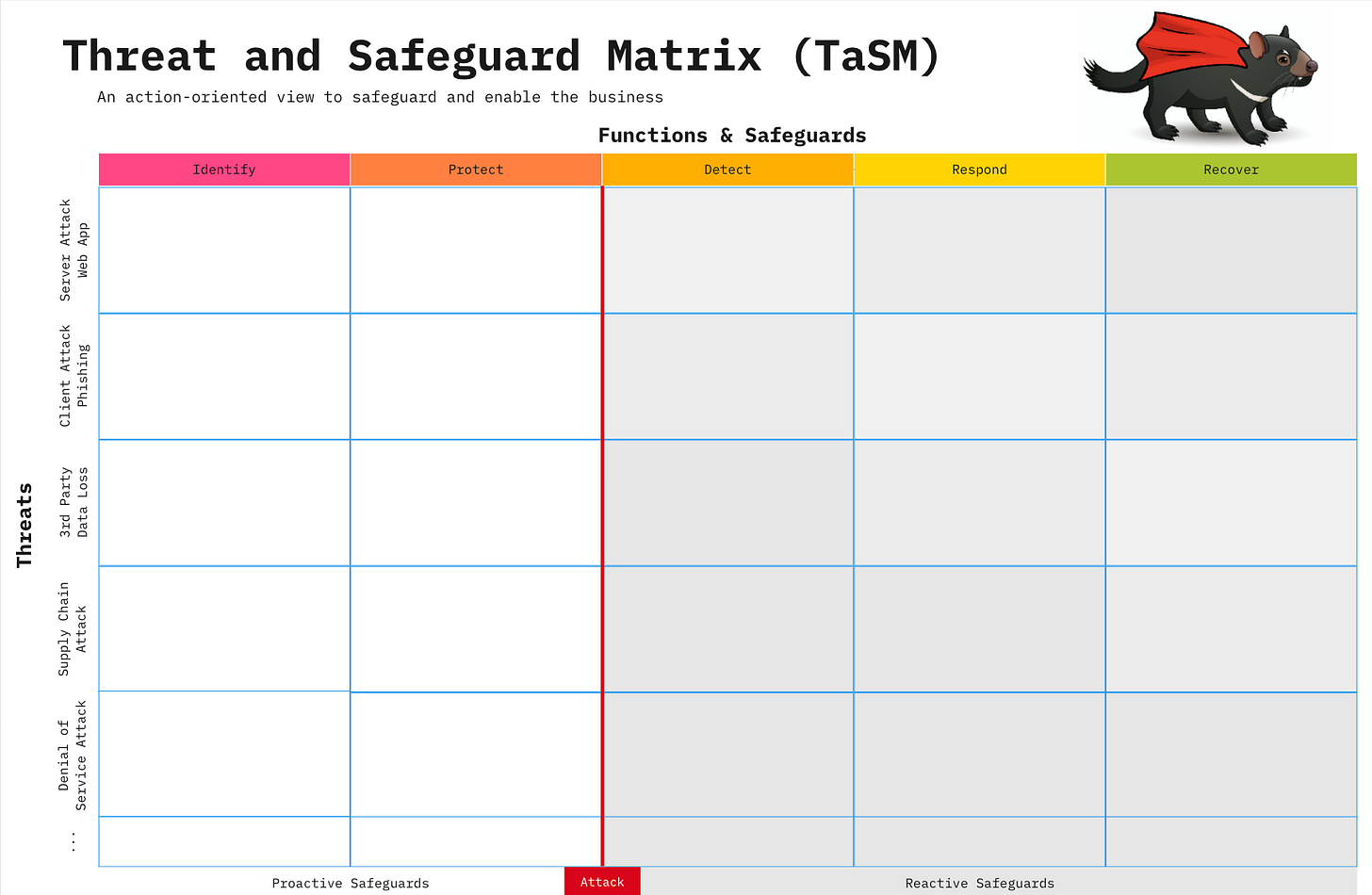
This framework is the OWASP Threat and Safeguard Matrix (TaSM).
Note the TaSM Website: https://owasp.org/www-project-threat-and-safeguard-matrix/
Unlocking the Power of the OWASP TaSM: What It Is and Why It's Revolutionary
The TaSM isn't just another buzzword; it's an evolutionary leap in cybersecurity communication and planning. Young built upon existing models, notably Sounil Yu's Cyber Defense Matrix, which maps security solutions against technical layers (application, data, network) and the NIST five functions (Identify, Protect, Detect, Respond, Recover). While helpful for technical discussions, Young realized that these technical layers often failed to engage organizational leaders like the Chief Financial Officer or Chief Audit Officer.
Here's the revolutionary shift: Instead of technical layers, the TaSM places "material threats to our company" as the core focus for its rows. This simple yet profound change transforms the conversation. Now, you can directly address how your organization will:
Identify
Protect
Detect
Respond
Recover ...from specific, actionable threats that resonate with business leaders.
Think about it: discussing "web application attacks" or "phishing attacks" or "CEO impersonation" is far more impactful to a CFO than talking about "application layer vulnerabilities". This customizable model allows you to prioritize threats based on your organization's unique concerns and threat intelligence.
Within each cell of the matrix, you populate it with "safeguards". A safeguard is a broad term, not just a technical product. It can be a:
Tool: Like allow-listing software or an EDR.
Process: Such as defined workflows for code review or vulnerability management.
Human: Including oversight, training, or specific roles.
TaSM in Action: Navigating a "Click Fix" Scenario
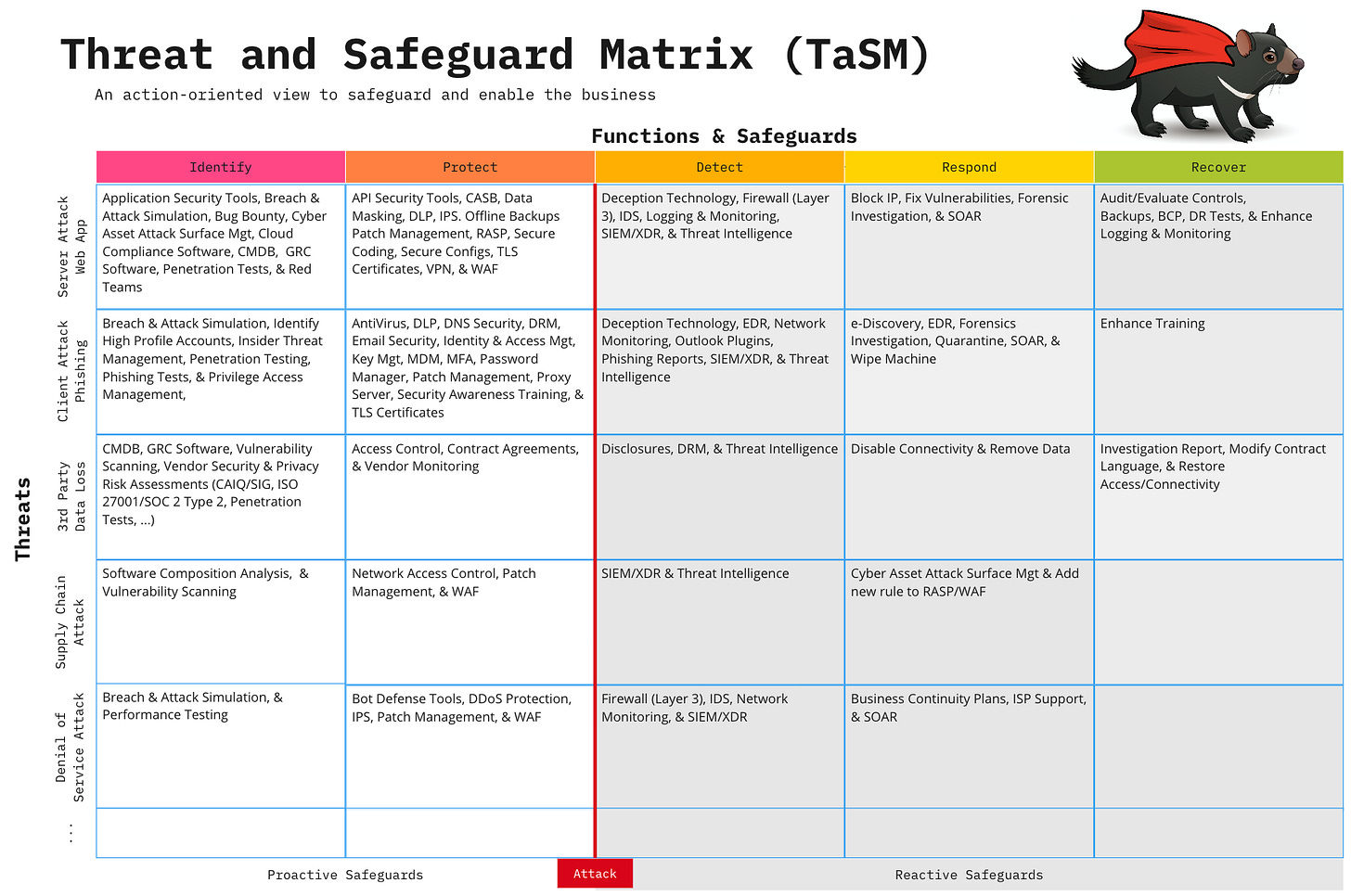
Let's illustrate the TaSM's practical application with a common threat: a "Click Fix" scenario where users are tricked into running malicious PowerShell scripts.
Identify: How do you recognize the potential for this threat?
Map your assets: Where could this happen? Think endpoints where users can input applications or scripts, or even servers. A robust system inventory or Configuration Management Database (CMDB) is crucial here.
Assess vulnerabilities: Identify weaknesses, such as developers having the ability to write custom PowerShell scripts on their machines, which could be exploited through phishing.
CISO Recommendation: Routinely inventory all assets and map potential entry points for common attack vectors. Understand not just what you have, but where your vulnerabilities lie in user behaviors and system configurations.
Protect: What proactive measures can you implement before an attack occurs?
Allow-listing software: Solutions like ThreatLocker can prevent unauthorized scripts from running unless they've been reviewed and approved.
Network controls: Block access to unusual top-level domains (e.g., .xyz) or newly registered domains, which are often used by attackers. Tools like ZScaler or Umbrella can enforce these policies.
CISO Recommendation: Implement strong preventive controls that go beyond traditional antivirus. Focus on application allow-listing and intelligent network filtering to block known malicious sources and behaviors before they can cause harm.
Detect: How do you spot the threat if it materializes?
Endpoint Detection and Response (EDR) and Security Information and Event Management (SIEM): Tools like CrowdStrike or Windows Defender can provide telemetry on script execution, feeding into your SIEM for analysis.
Logging: Monitor Windows logging features, application server logs, and command history for suspicious activities like unusual PowerShell script execution or access to strange websites.
CISO Recommendation: Invest in robust EDR and SIEM solutions, and ensure comprehensive logging is enabled across your environment. Define specific alerts for unusual user behavior or system activities that deviate from baselines.
Respond: What immediate, temporary actions do you take upon detection to contain the damage?
Containment: Temporarily disable PowerShell scripts company-wide to stop the spread if the severity is unknown.
Review access: Immediately assess who has permissions that could be exploited.
CISO Recommendation: Develop clear, actionable incident response playbooks that prioritize containment. Practice these scenarios regularly to ensure your team can execute swift, temporary measures to limit the blast radius of an attack.
Recover: How do you resume normal operations and address the root cause to prevent recurrence?
Resumption: Carefully re-enable authorized PowerShell scripts, potentially one by one, after review.
Root cause remediation: Change roles or permissions that were exploited.
Rebuild, don't just restore: For severe incidents like data encryption, "blow away" compromised servers and deploy new, fully patched ones rather than risking residual infection from an attempted restoration.
CISO Recommendation: Go beyond just getting operations back online. Focus on thorough root cause analysis and implementing permanent fixes. Prioritize rebuilding secure environments over attempting risky restorations for heavily compromised systems.
Beyond Cyber: Expanding TaSM's Impact Across Your Organization
The TaSM's genius lies in its versatility, offering profound benefits that extend far beyond tactical cybersecurity responses.
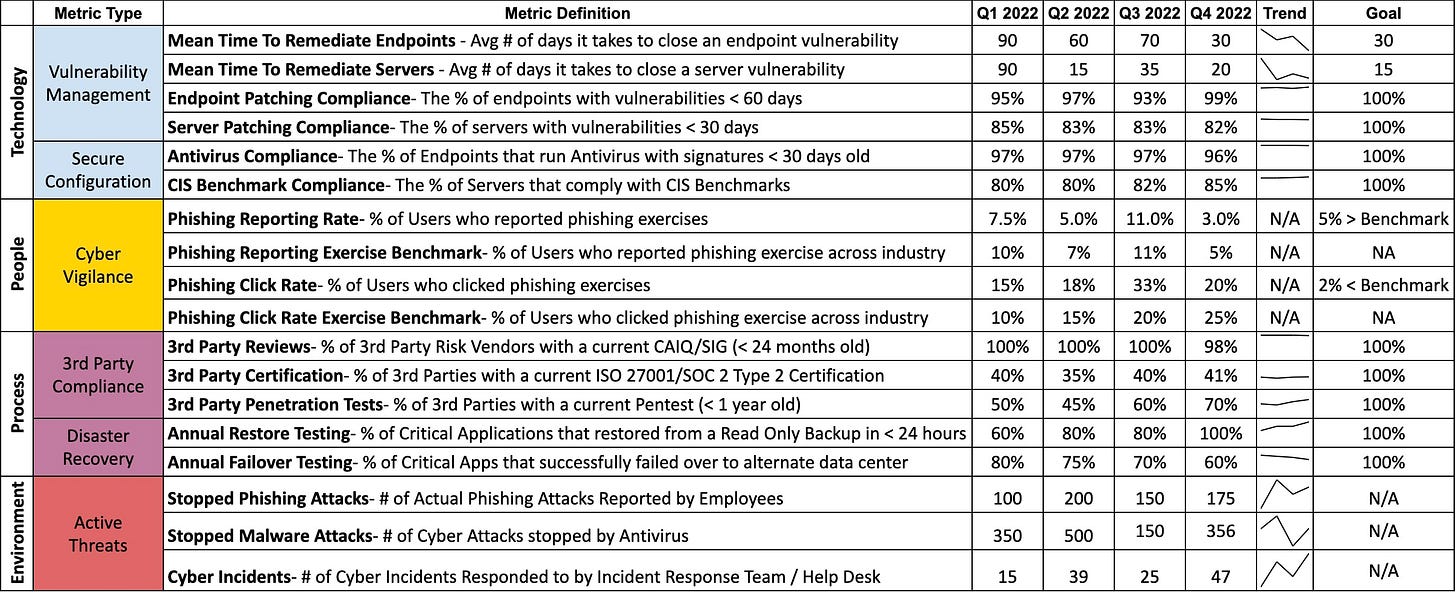
Driving Budget & Resource Justification with a "Cyber Report Card":
By populating the TaSM, CISOs can create a "cyber report card" that demonstrates measurable results for addressing specific threats.
Track progress using trend analysis (e.g., patching times) against organizational Service Level Agreements (SLAs). Showing improvement (e.g., patching time from 50 days to 10 days) is a clear win. Conversely, a worsening trend demands immediate attention and can justify increased funding.
This allows you to show where you're meeting, or exceeding, organizational risk tolerance, enabling you to drive a push for funding and capabilities.
CISO Recommendation: Develop clear, quantifiable metrics for your safeguards within the TaSM. Present these metrics as a "cyber report card" to your executive leadership, focusing on trends and adherence to agreed-upon SLAs to advocate for budget and resources.
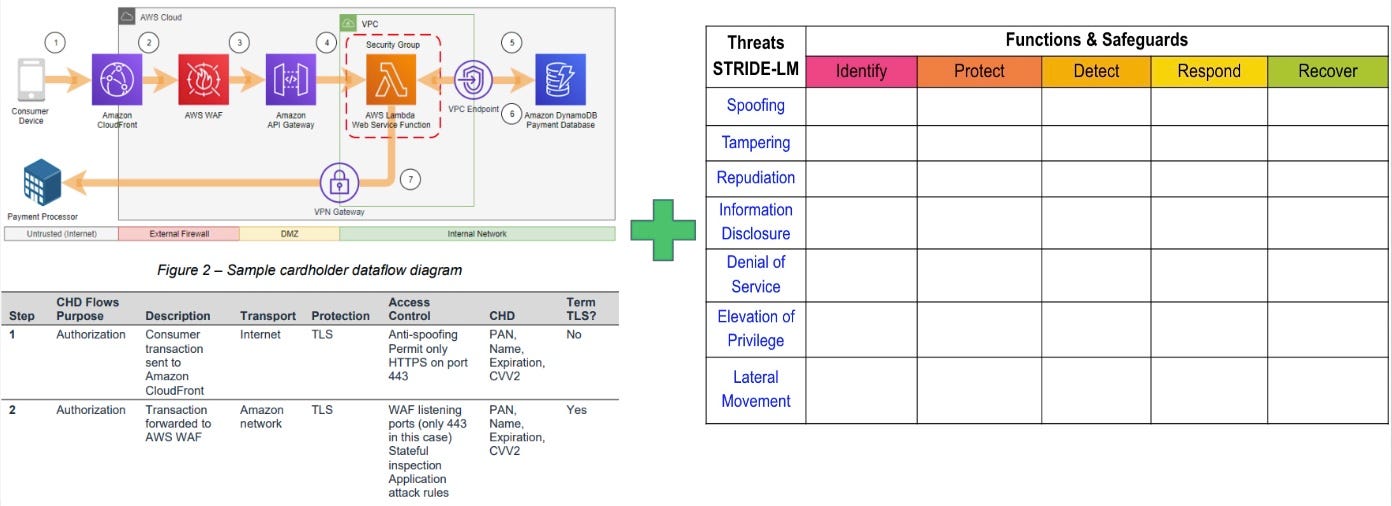
Enhancing Threat Modeling for Enterprise-Wide Security:
TaSM brings much-needed consistency to threat modeling. Instead of ad-hoc approaches, you can combine a simple data flow diagram with a review against common application threats using frameworks like STRIDE (Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, Elevation of privilege).
This structured method helps identify common enterprise-level weaknesses across applications, informing future budget planning and architectural reviews. You can spot recurring mistakes that need an enterprise-wide fix rather than addressing them individually for each application.
CISO Recommendation: Standardize your threat modeling process using the TaSM framework, combining data flow diagrams with common threat categories like STRIDE. This will help you identify systemic weaknesses across your application portfolio and advocate for enterprise-level architectural improvements.
Transforming Organizational Risk Management:
This is arguably the TaSM's most powerful feature: its ability to transcend cyber and integrate with broader organizational risk management.
You can include material threats from various departments – financial threats (like changing interest rates), HR threats (insider risks, foreign employee concerns), or legal/regulatory compliance issues.
By ranking all material threats (not just cyber), you can demonstrate where cyber risks truly stand within the broader organizational risk landscape. This helps build a coalition of support, where legal, HR, and finance leaders advocate for cybersecurity spending, recognizing it addresses top company risks.
It also teaches a "cyber mentality" (Identify, Protect, Detect, Respond, Recover) to non-cyber departments, enhancing overall organizational security acumen and enabling CISOs to earn their "C" as a chief officer.
CISO Recommendation: Collaborate with other departmental leaders (Finance, HR, Legal) to populate the TaSM with their material threats. Present a holistic view of organizational risk where cyber threats are positioned alongside other business risks. This builds powerful alliances and ensures cybersecurity is seen as a business enabler, not just a cost center.
Addressing Emerging Risks, Including AI:
The TaSM is highly applicable to emerging threats like Artificial Intelligence (AI) risks.
Different AI risks, such as sensitive data leaks versus hallucination problems, require distinct safeguards, tools, and processes. The TaSM helps map these varied solutions effectively.
CISO Recommendation: As new technologies like AI emerge, immediately apply the TaSM framework to identify and categorize specific risks. Recognize that diverse AI risks will require tailored safeguards, tools, and processes, and plan your defense strategy accordingly.
Your Call to Action: Embrace the TaSM Today!
The OWASP Threat and Safeguard Matrix (TaSM) offers a powerful, intuitive, and universally understandable way to grasp, plan for, and effectively communicate about cybersecurity threats. It shifts discussions from technical jargon to what truly matters to the business, empowering you to better secure your organization and justify your vital work.
Ready to revolutionize your cybersecurity approach and transform your budget discussions? You can easily find the OWASP Threat and Safeguard Matrix on owasp.org or by simply Googling "OWASP TaSM". Explore it today and start building a more secure, strategically aligned, and better-understood defense for your organization!